iSecurity Assessment
The iSecurity Assessment offers an in depth look into the security of your IBM i and enables you to understand potential vulnerabilities and areas of concern in regard to various aspects of IBM iSecurity. The iSecurity Assessment provides a detailed report, telling you want you need to know about potential threats and vulnerabilities on your IBM i system.
The assessment installs and runs in five minutes or less, and generates a report only you can see. Once completed, you'll have a consultation with one of our IBM i/AS400 security specialists who will help you better understand the results of your assessment, provide details into industry best practices, and give you suggestions and options to secure your IBM i system.

Determines if proper controls and remote activity controls are in place

Identifies if there are too many high-level access users on your IBM i

Facilitates identifying breaches in real time

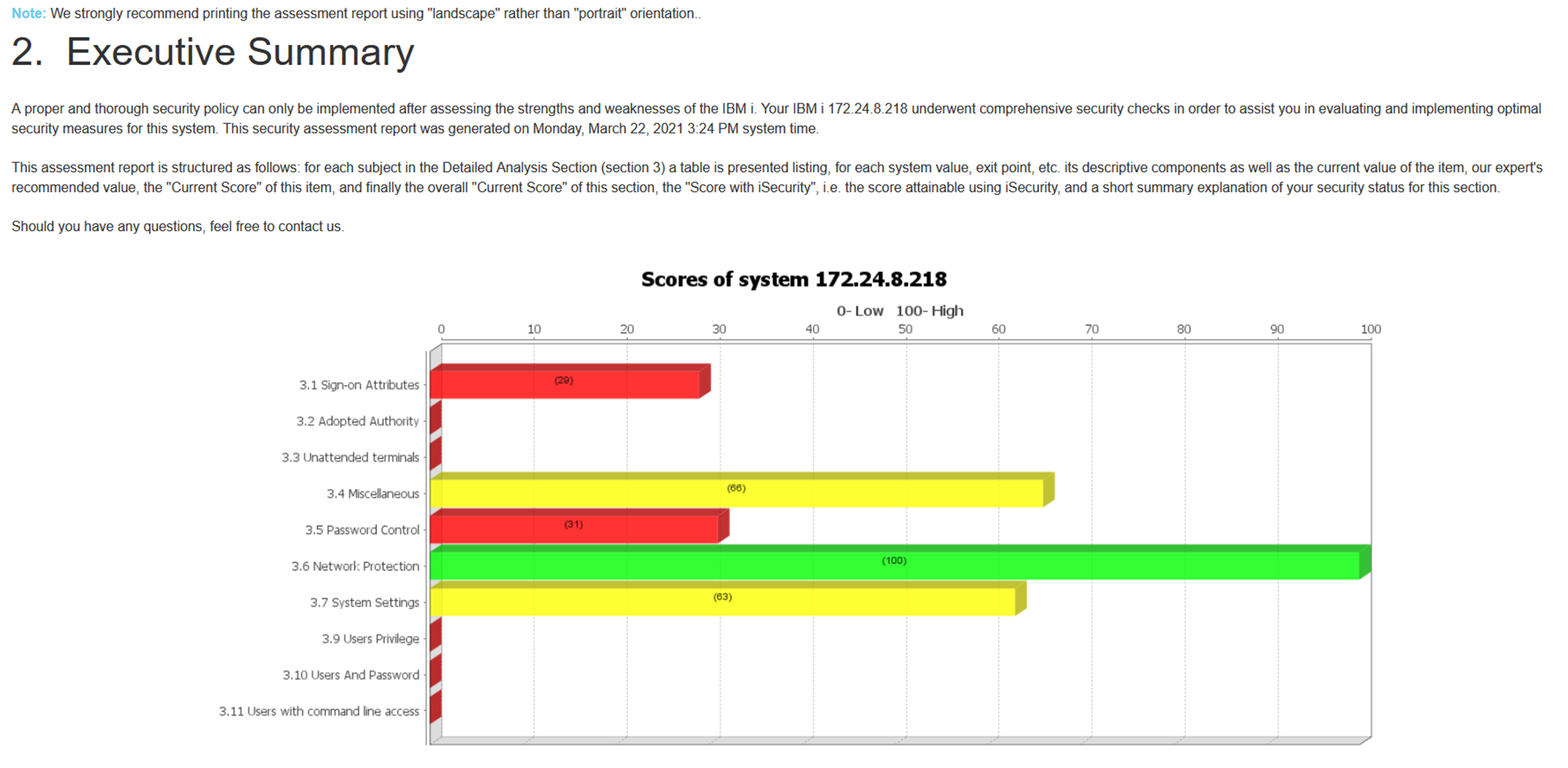
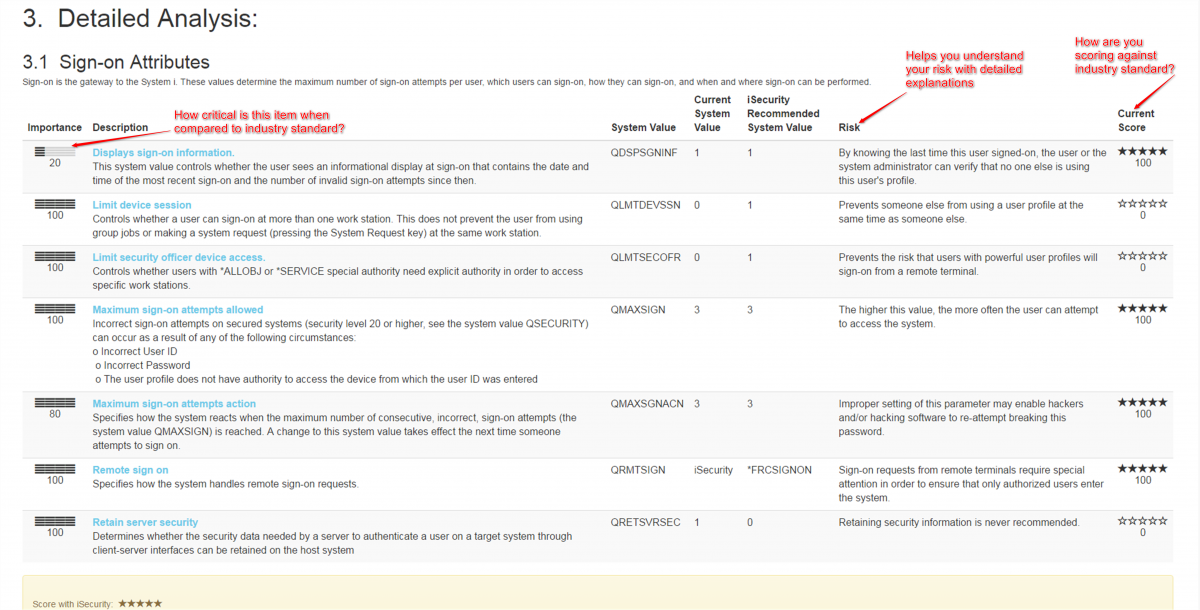
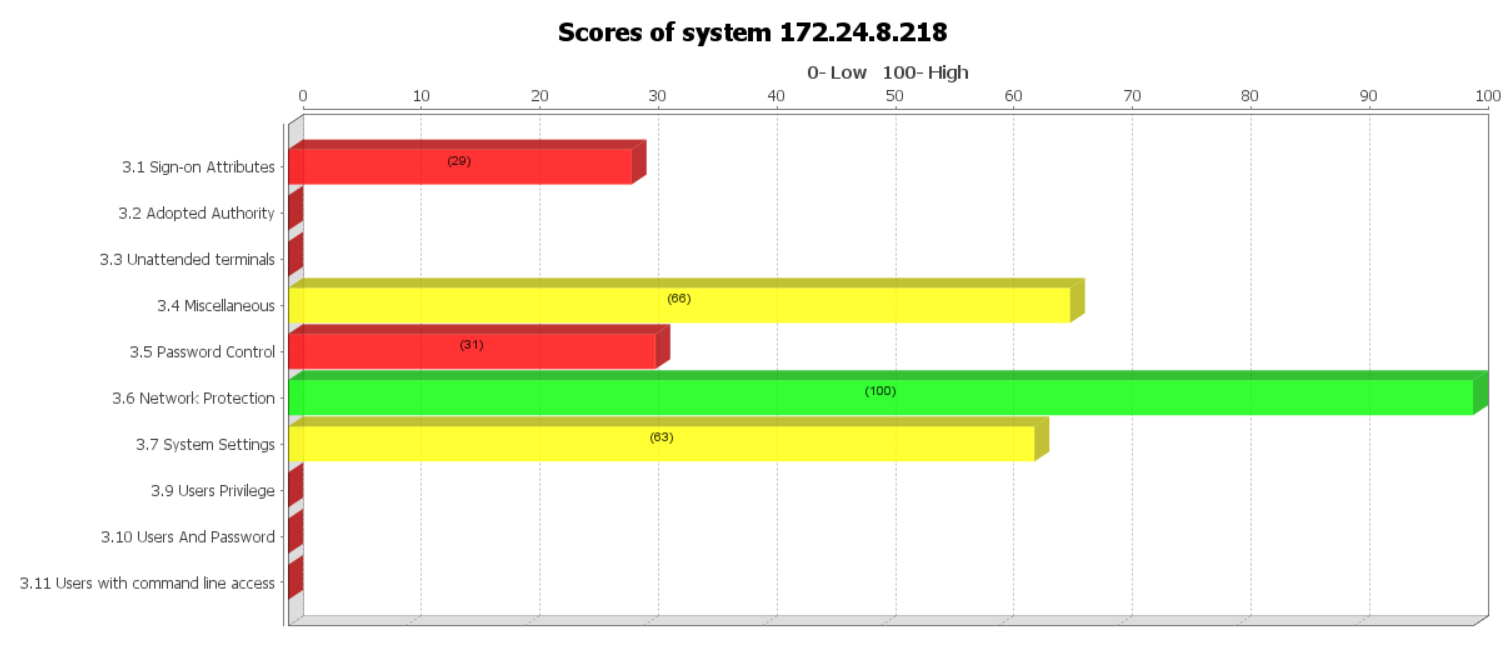
Identifies potential threats and vulnerabilities on your IBM i system

Provides recommended solutions to remediate identified security shortcomings
 READ PRODUCT SHEET
READ PRODUCT SHEET