iSecurity Encryption
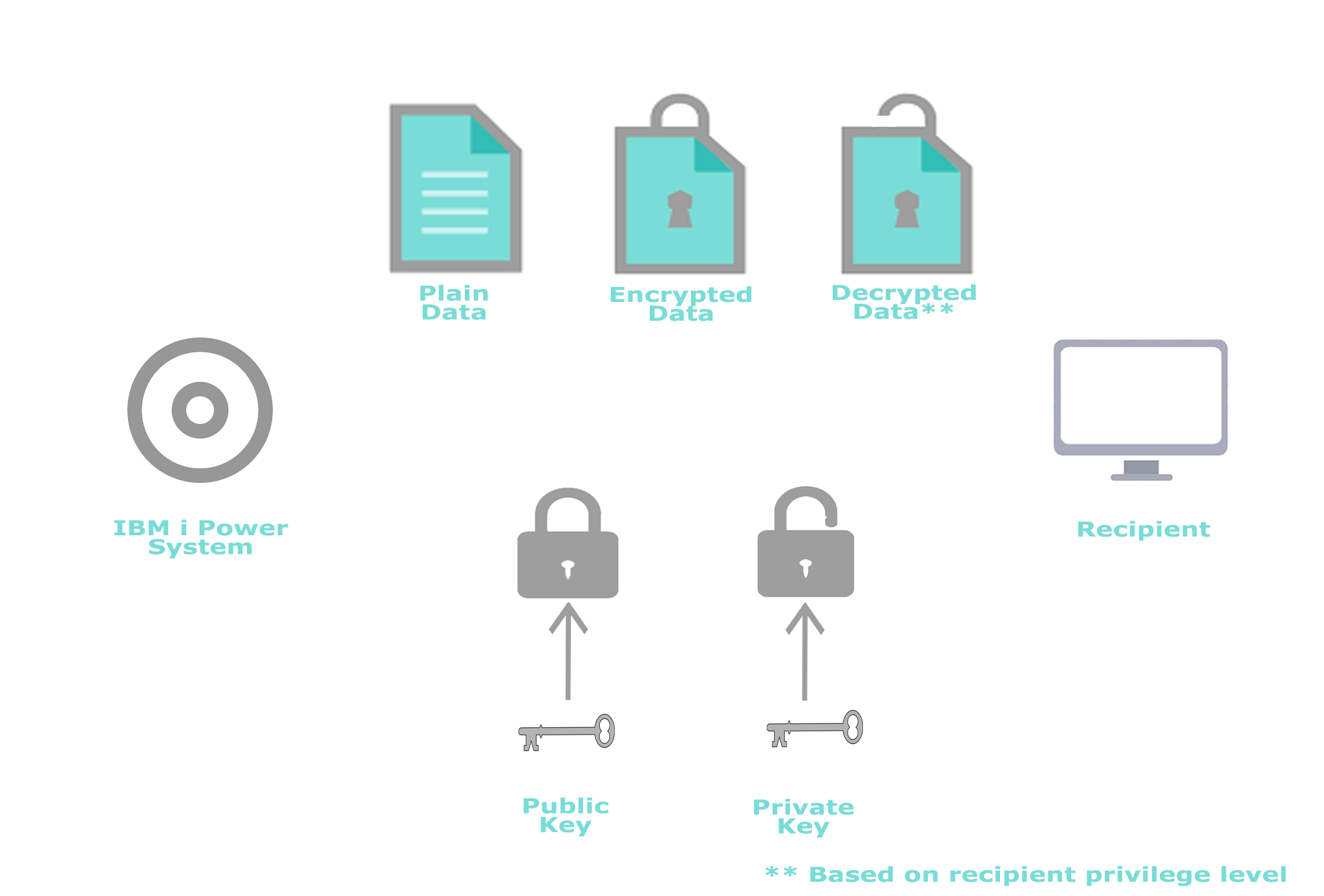
Data encryption is an essential element of effective IBM i security. It is the final layer of protection for all business-critical data, making data meaningless to anyone passing through other protection layers.
To stay in compliance with PCI-DSS, HIPAA, GDPR, SOX, and other regulatory bodies, sensitive parts of your data are required to be encrypted, ensuring the safety of your company and customer's critical information.
The iSecurity Encryption solution, part of the iSecurity suite, allows you to adequately protect all sensitive data and meet your compliance and regulatory requirements.

Encryption at Rest and/or in Transit for IBM i data

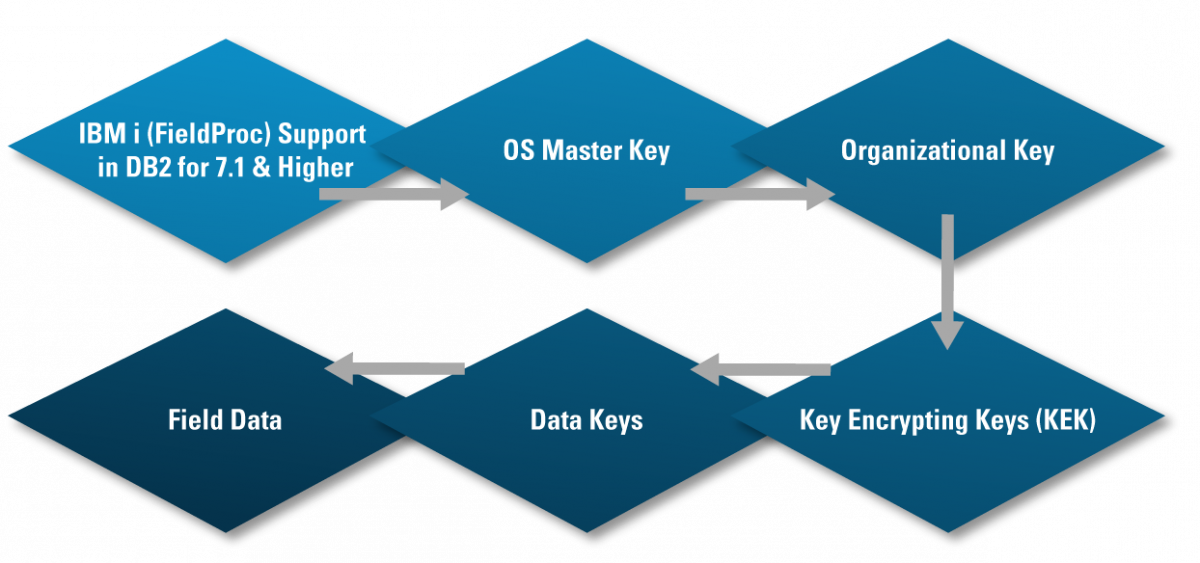
Fully automated encryption, taking advantage of built-in IBM i Field Level Encryption

Fulfills Audit and Compliance requirements

Built on modern technology without having to maintain compatibility with legacy encryption tools

Uses industry standard AES-256 encryption
 READ PRODUCT SHEET
READ PRODUCT SHEET