New Guide Shows You How to Deploy IBM i MFA
Learn everything you need to know about deploying MFA in an IBM i environment!
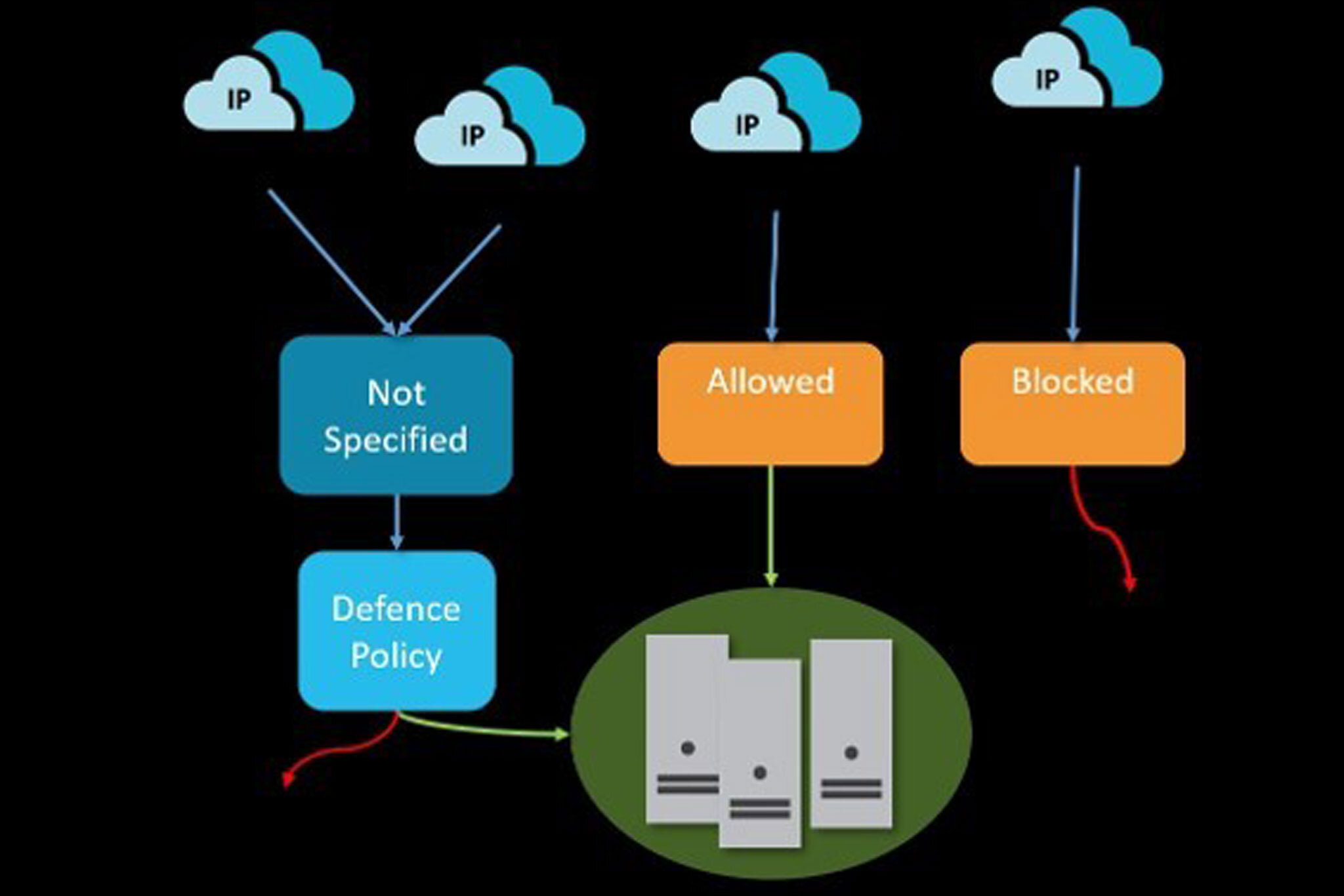
iSecurity Multi Factor Authentication
iSecurity Multi Factor Authentication (MFA) provides increased security for users by adding another layer of identity verification to your IBM i resources.
When implemented, users are required to further identify themselves beyond using just a password, strengthening your systems against unauthorized access.
Companies, cyber insurance carriers, industry regulators and governments are realizing the importance of layered access security and have begun mandating implementation of MFA.
iSecurity MFA helps you comply with those requirements without imposing unnecessary workloads on your user base.

Strengthens IBM i access security

Enhances the safety of business information

Meets governmental, regulatory and insurance requirements

100% Native IBM i installation. No external servers needed

Reduces the risk of account takeovers
 READ PRODUCT SHEET
READ PRODUCT SHEET