Security and Compliance
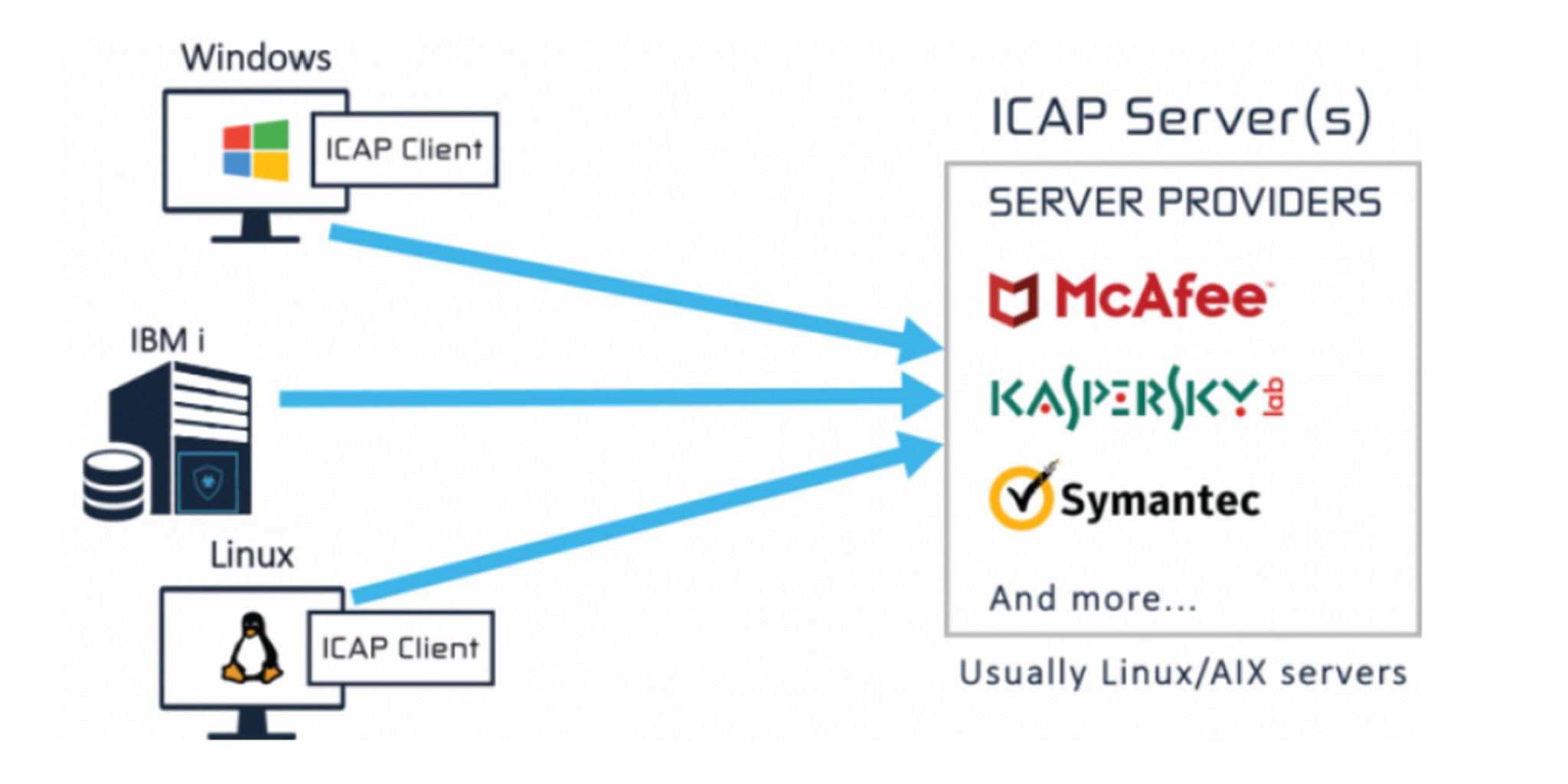
Although the IBM i does not run .exe files, it can house infected files in its Integrated File System (IFS), where they can silently wait until someone on the network transfers and opens that file on their PC.
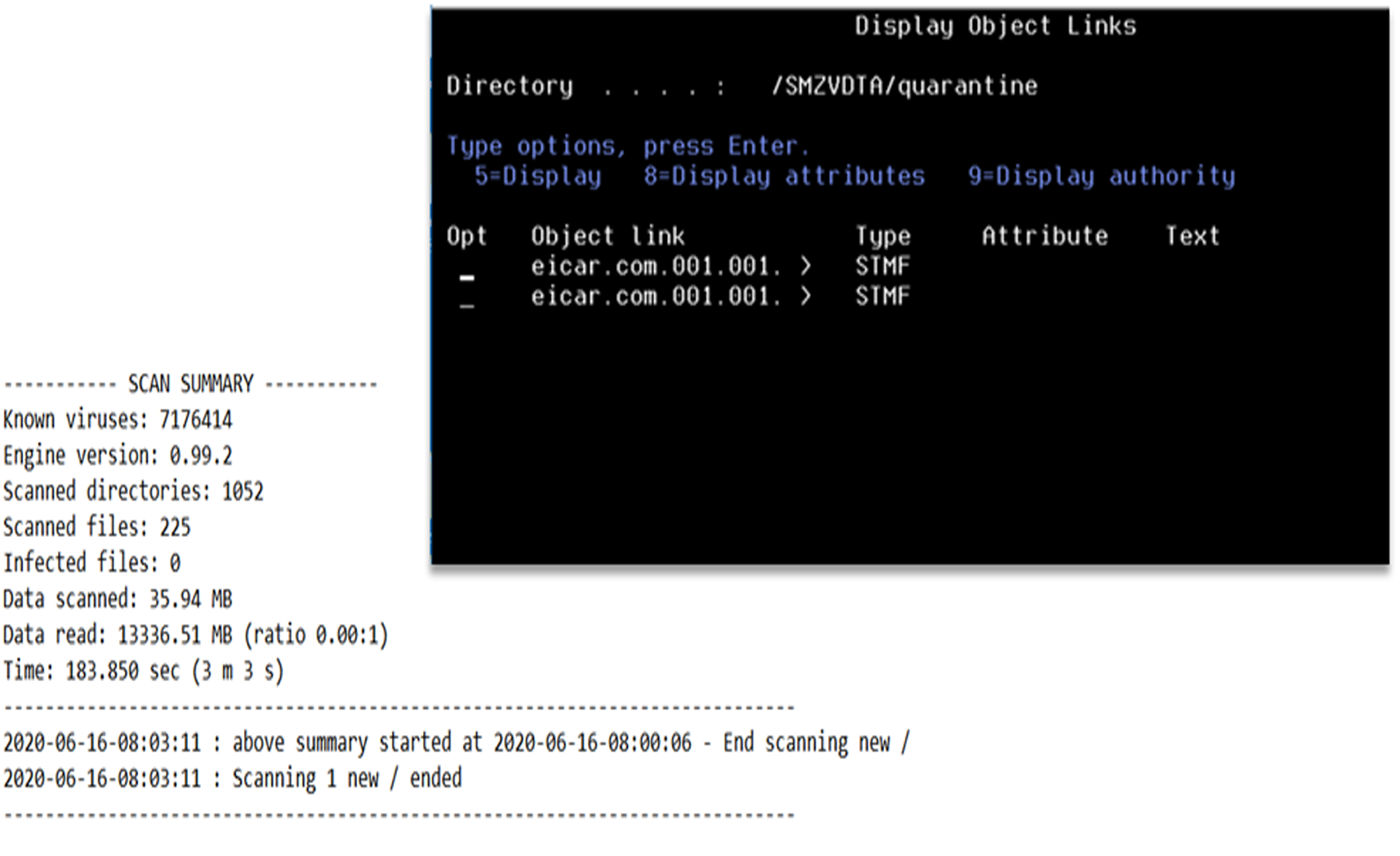
iSecurity Anti-Virus enables you to detect and quarantine infected IFS files, helping to keep viruses away from your network and your PC’s and servers.

Prevents your IBM i IFS from becoming an infection source

Scans IFS objects before and/or after they are used

Built in scheduler enables planned IFS virus scanning

E-mail and SMS text message can be sent when a virus is detected.

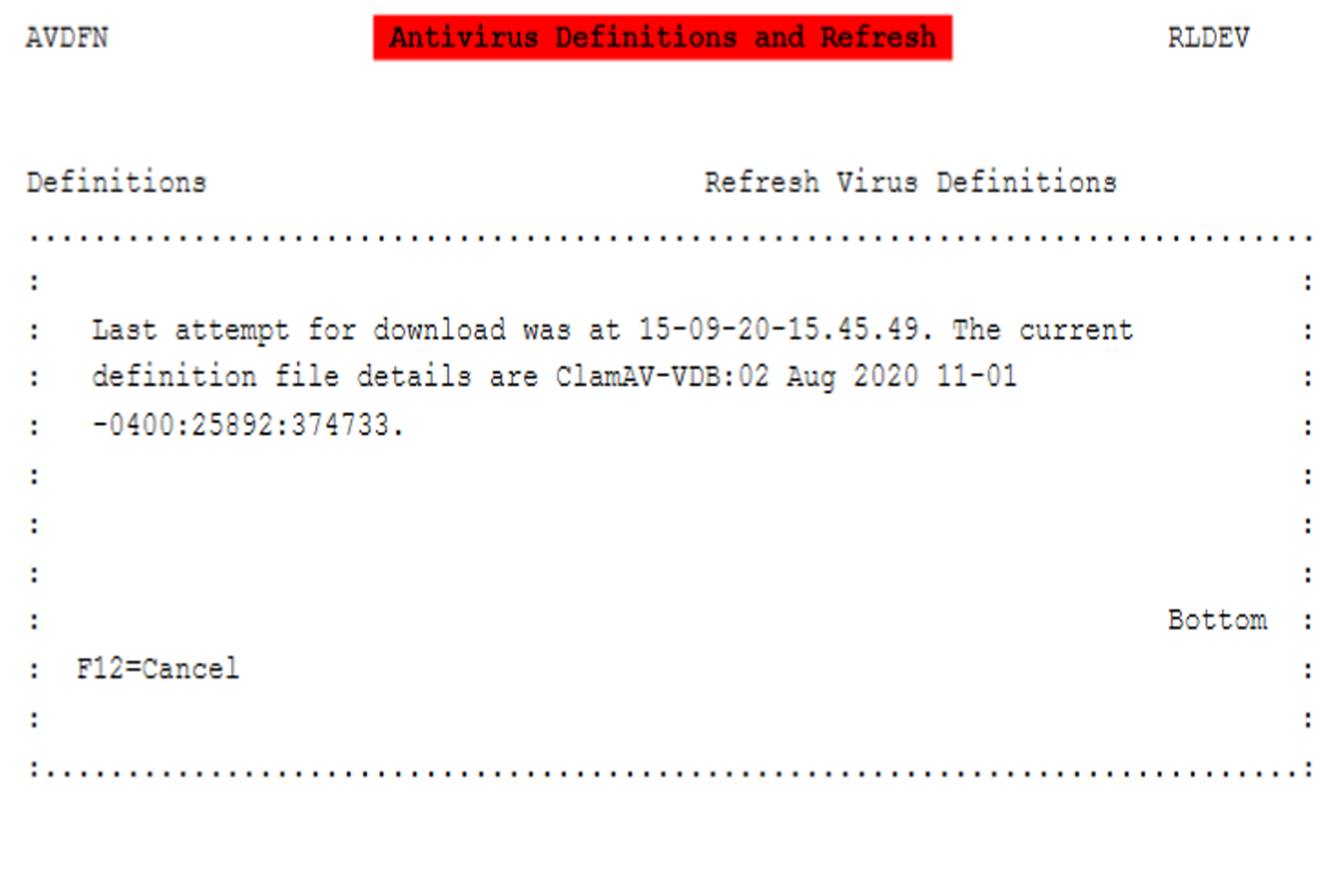
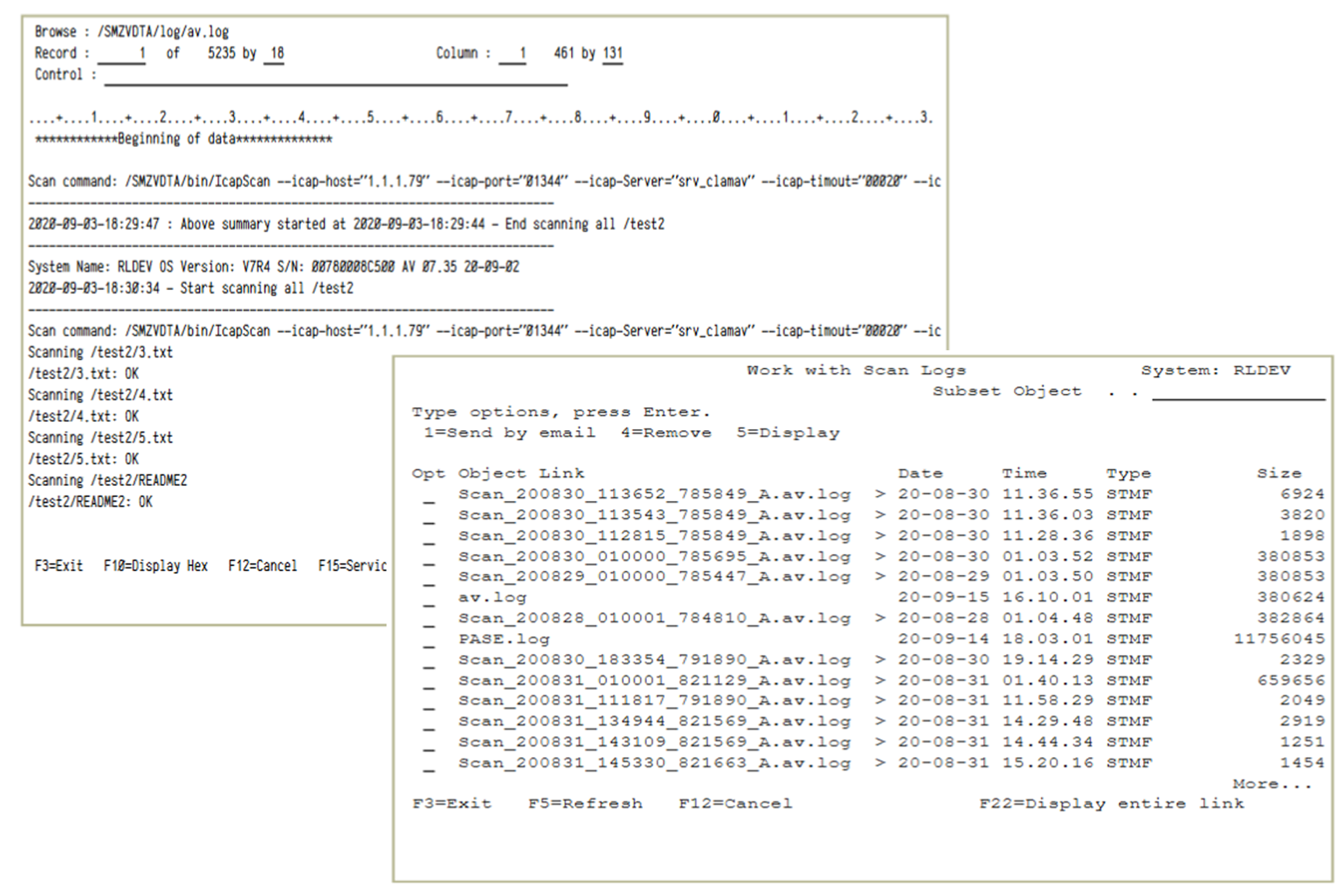
Maintains historical logs of virus activity and scanned objects for review and analysis
 READ PRODUCT SHEET
READ PRODUCT SHEET