Guide to Managing IBM i Security with Exit Points
Learn how to use exit points to enable IBM i firewall capabilities and to extend i operating system functionality
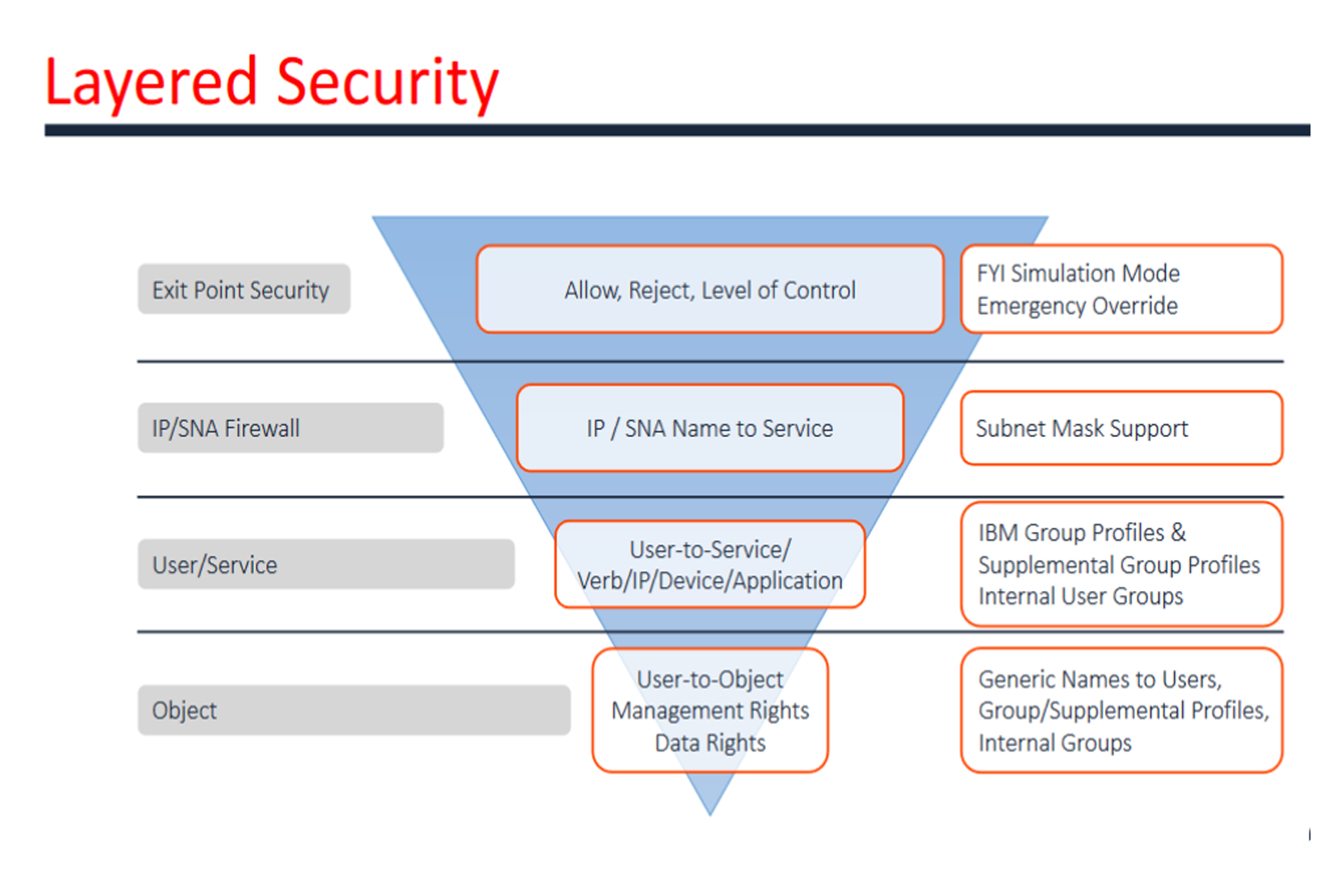
iSecurity Firewall
iSecurity Firewall protects and secures remote access to and from the IBM i.
Firewall enhances the native IBM i by controlling access via known external sources and controlling precisely what users are permitted to do once access is granted.
Access rules can be generated and run in simulation mode for testing or in full intrusion prevention mode for active protection.
Its powerful query generator satisfies reporting needs for auditing, governmental and regulatory requirements.
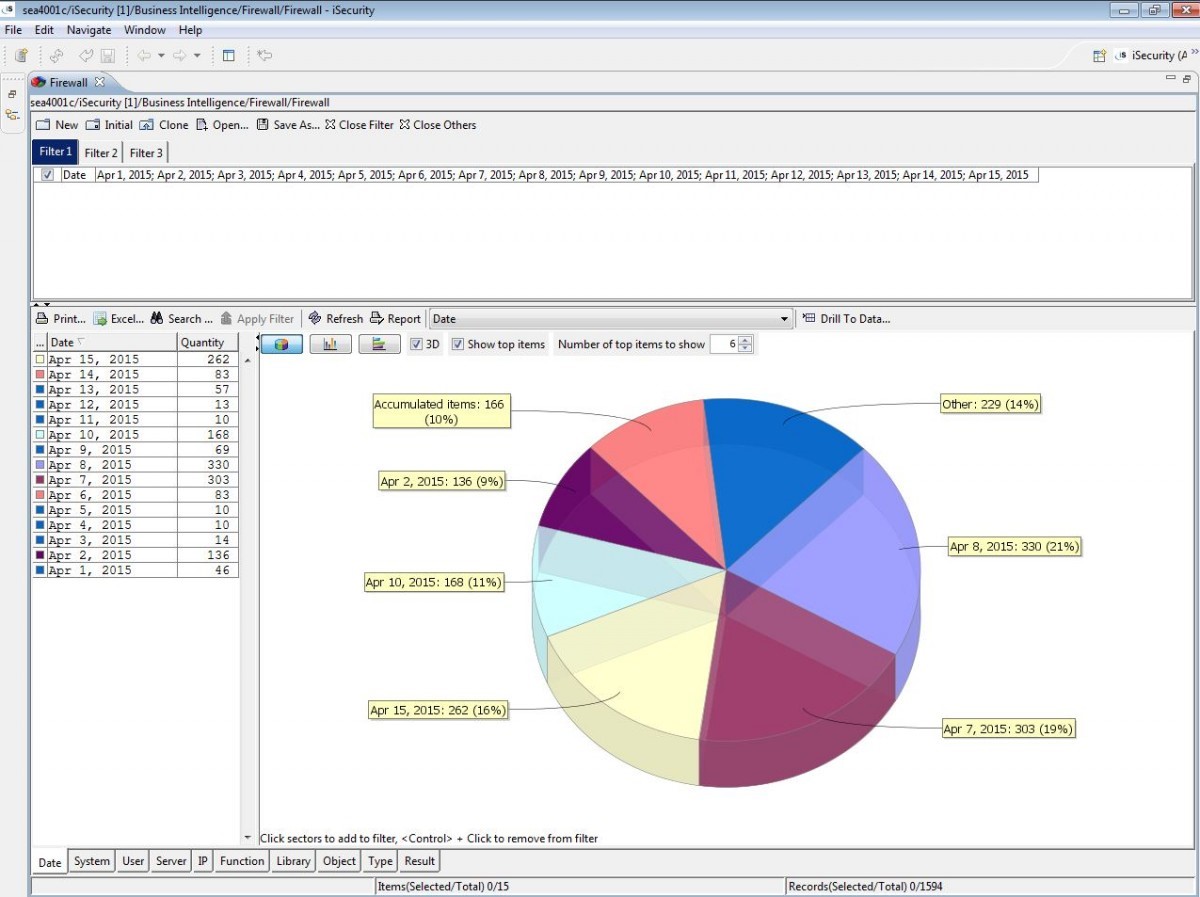
Firewall’s Visualizer Business Intelligence enables IT managers to graphically analyze security related system activity quickly and easily.

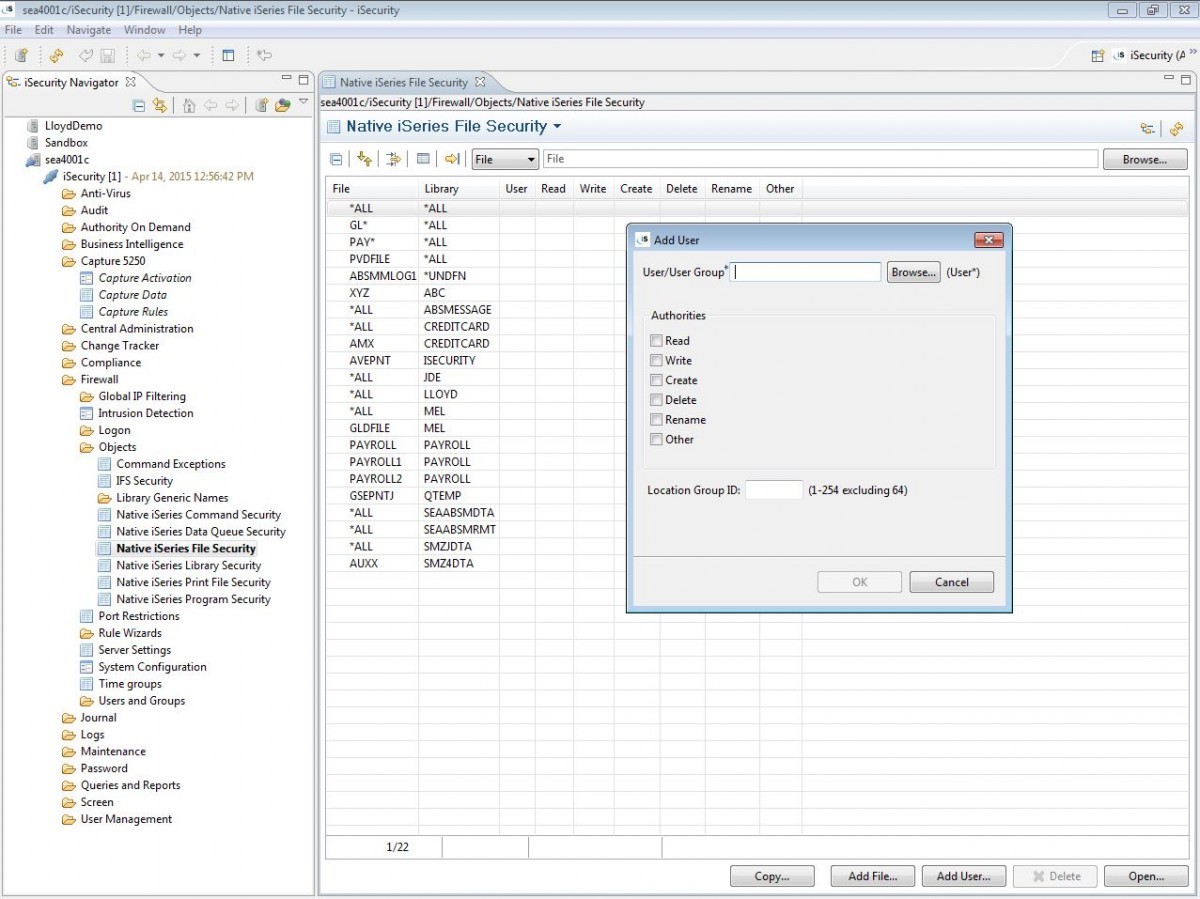
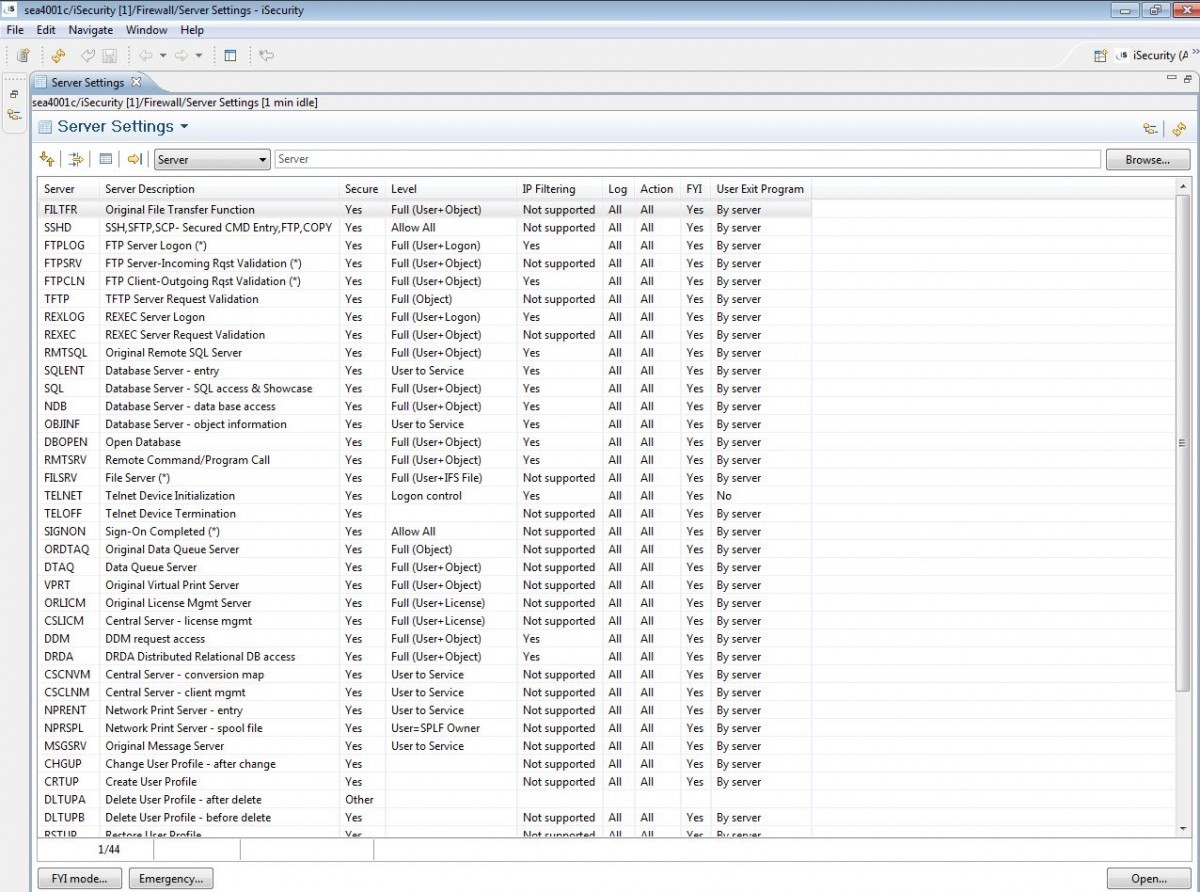
Protects security related IBM i exit points and servers

Precisely controls actions remote users may perform after access is granted

Simulation mode tests IBM i security plan before going live

Provides 100+ ready-to-run queries for reporting on remote user activity

Built-in Business Intelligence allows managers to graphically analyze security-related system activity
 READ PRODUCT SHEET
READ PRODUCT SHEET