What is iSecurity Command?
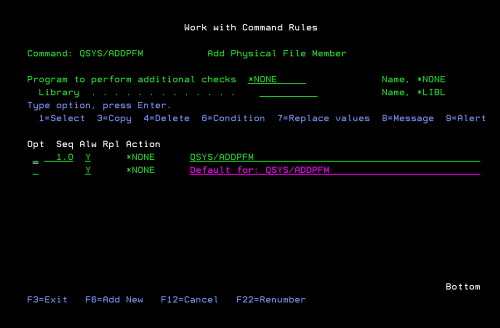
iSecurity Command monitors and filters commands and their parameters before they are run, enabling you to control each parameter, qualifier or element, in conjunction with the context in which it executes.
Command options include Allow, Allow with Changes, and Reject. The software consists of a comprehensive log, proactive alerting and easily integrates with SIEM.

Provides total control over system & user defined CL commands, regardless of how the command was entered

Makes defining command rules more flexible, as opposed to all-or-nothing approach to command security

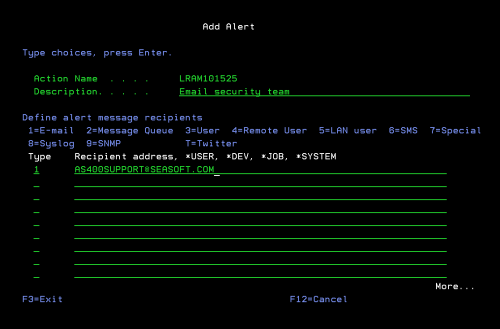
Real-Time Alerting enables companies to ensure command usage policies aren’t being violated

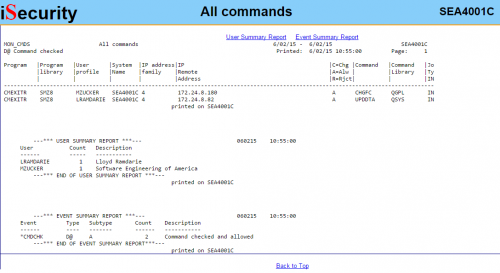
Full reporting capabilities provide that security compliance requirements are being met

Command usage logs can be viewed online or in IBM i outfile or output queues
 READ PRODUCT SHEET
READ PRODUCT SHEET