iSecurity AP-Journal
Application & Field Level Security Monitoring
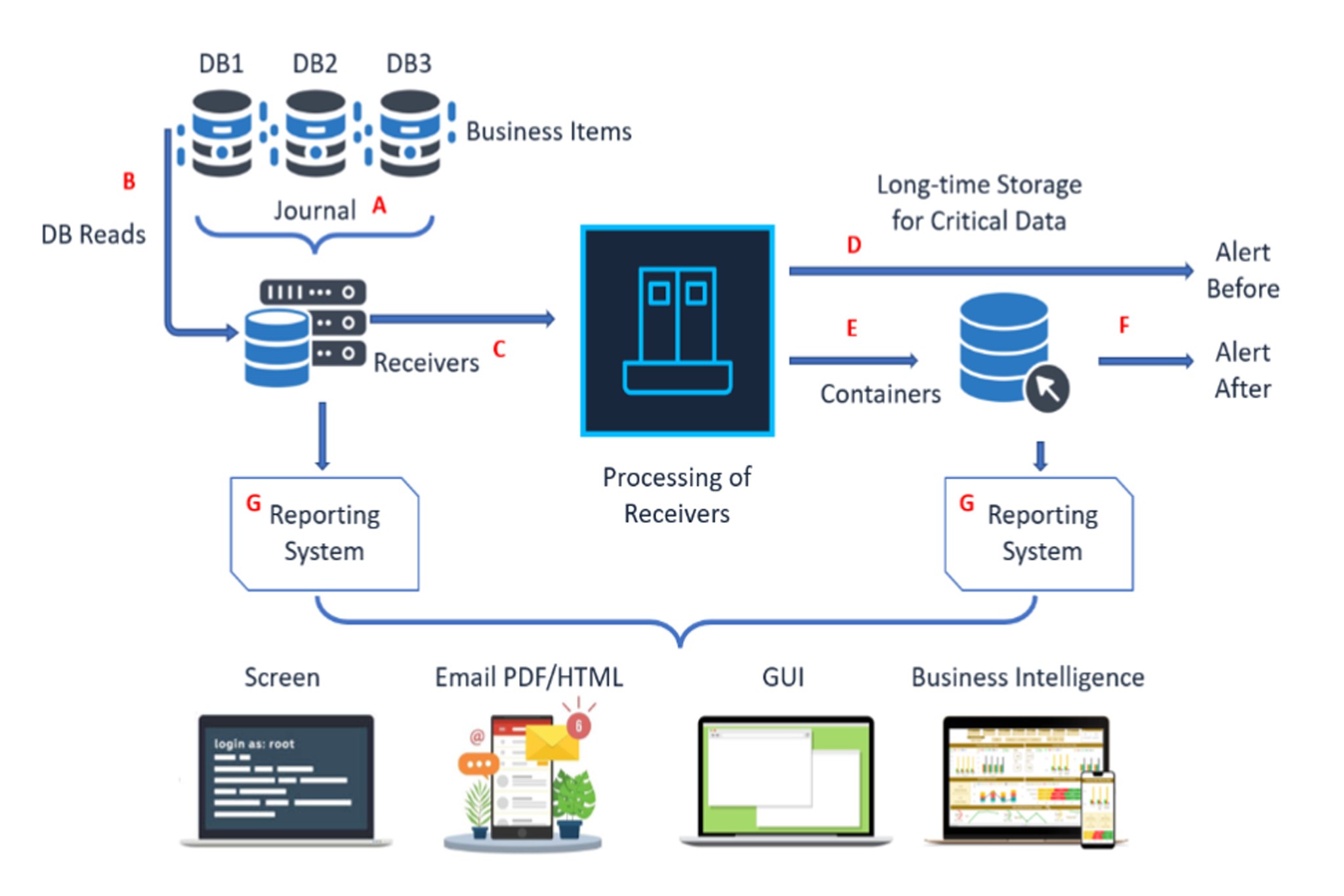
iSecurity AP-Journal is an Application Security and Business Analysis software solution for IBM i servers.
AP-Journal keeps managers closely informed of essential changes in their business-critical data and allows companies to monitor these entries and send alerts or perform actions if suspicious activity is identified.
iSecurity AP-Journal reacts to insider threats as well as external security breaches and preserves the integrity of business-critical information.

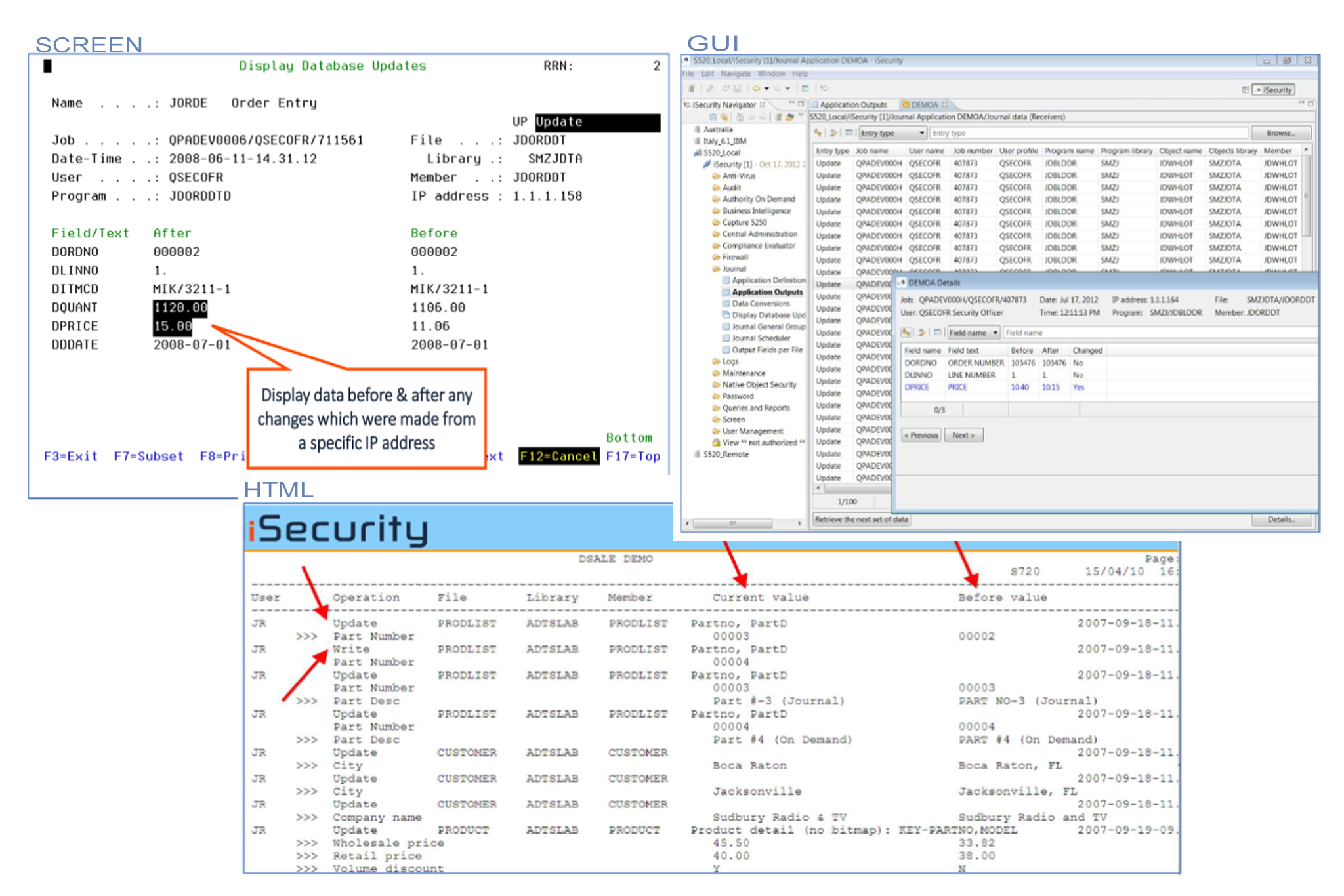
Provides timeline reporting for all changes relating to critical application data

Reduces unauthorized access to critical data and enables organizations to meet regulatory requirements

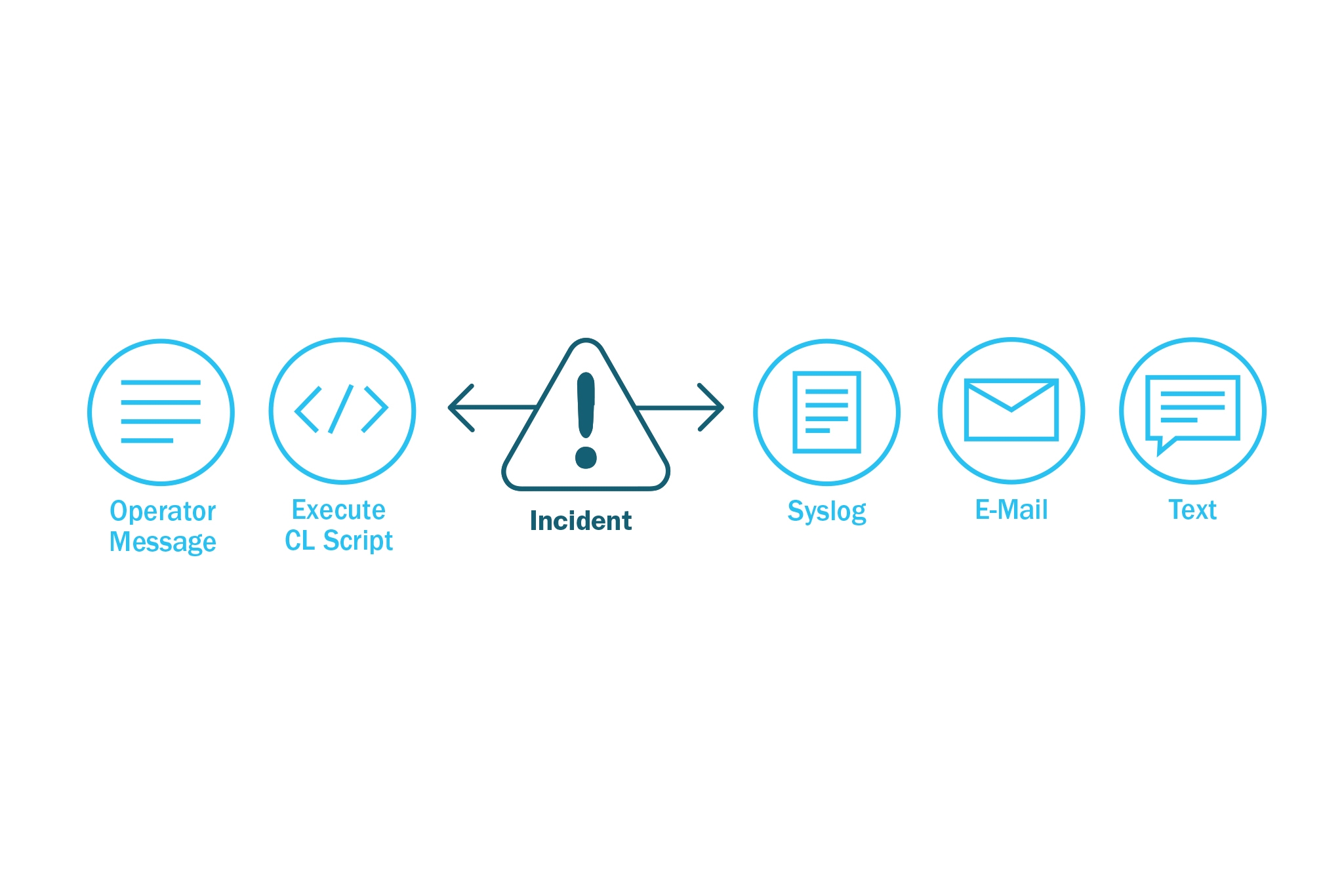
Issues real-time alerts informing managers of changes in application databases and/or unapproved access to critical data

Identifies suspicious activity and preserves the integrity of business-critical information

Enforces business rules by reacting to real-time events
 READ PRODUCT SHEET
READ PRODUCT SHEET