iSecurity Audit
iSecurity Audit provides unparalleled monitoring and Audit & Compliance reporting on activity and IBM iSecurity conditions, ensuring compliance with government regulations and industry & corporate standards.
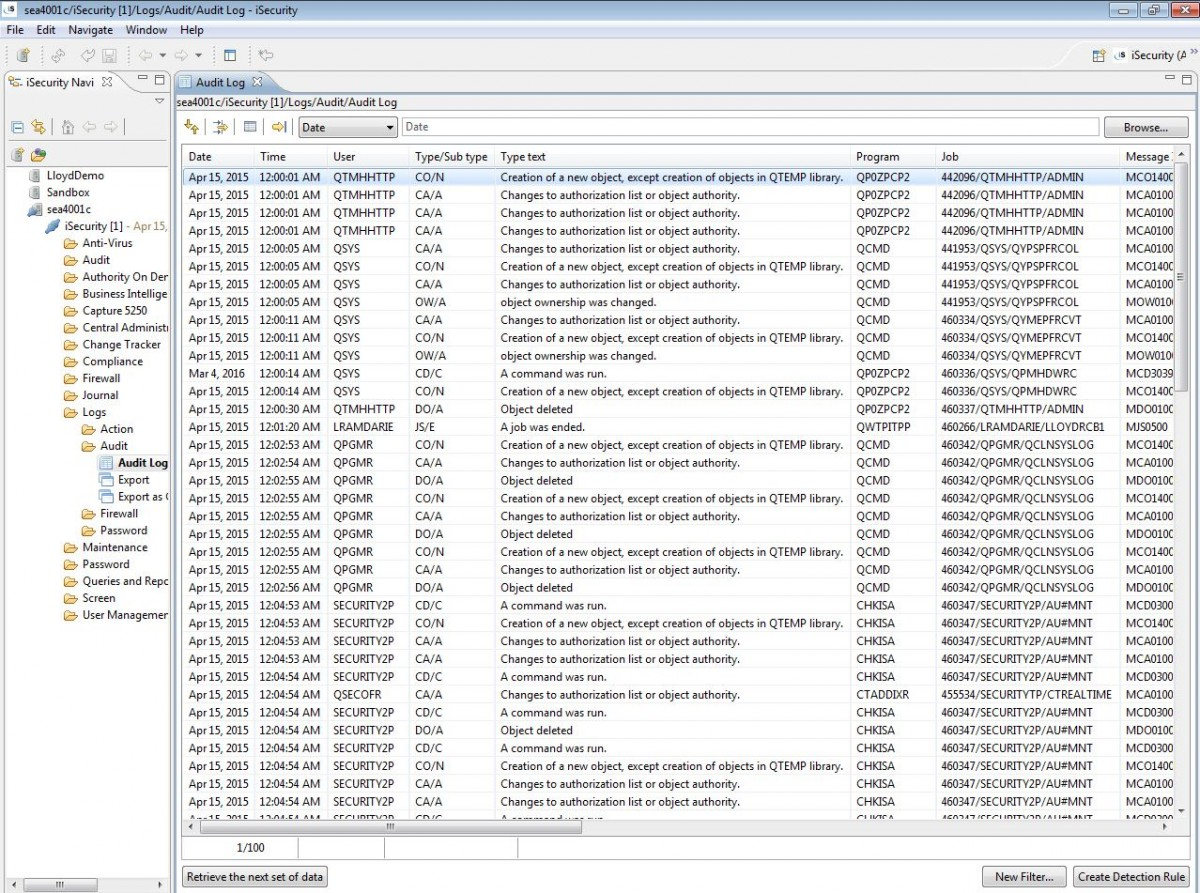
iSecurity Audit provides real-time monitoring of system related activities, generating alerts and initiating responses to potential threats for the IBM i.
iSecurity Audit’s powerful query and report generator provides data required in real-time or scheduled through the built-in scheduling tool. Audit is available in the native “green-screen” interface or a state-of-the-art GUI (Graphical User Interface) version.
iSecurity Audit is for local activity, please see iSecurity Firewall for monitoring remote activity.

Enables compliance with critical government, industry, and regulatory standards

Provides over 200 pre-defined reports covering common IBM i auditing & compliance scenarios

Powerful Query Wizard allows users to quickly and easily create audit reports

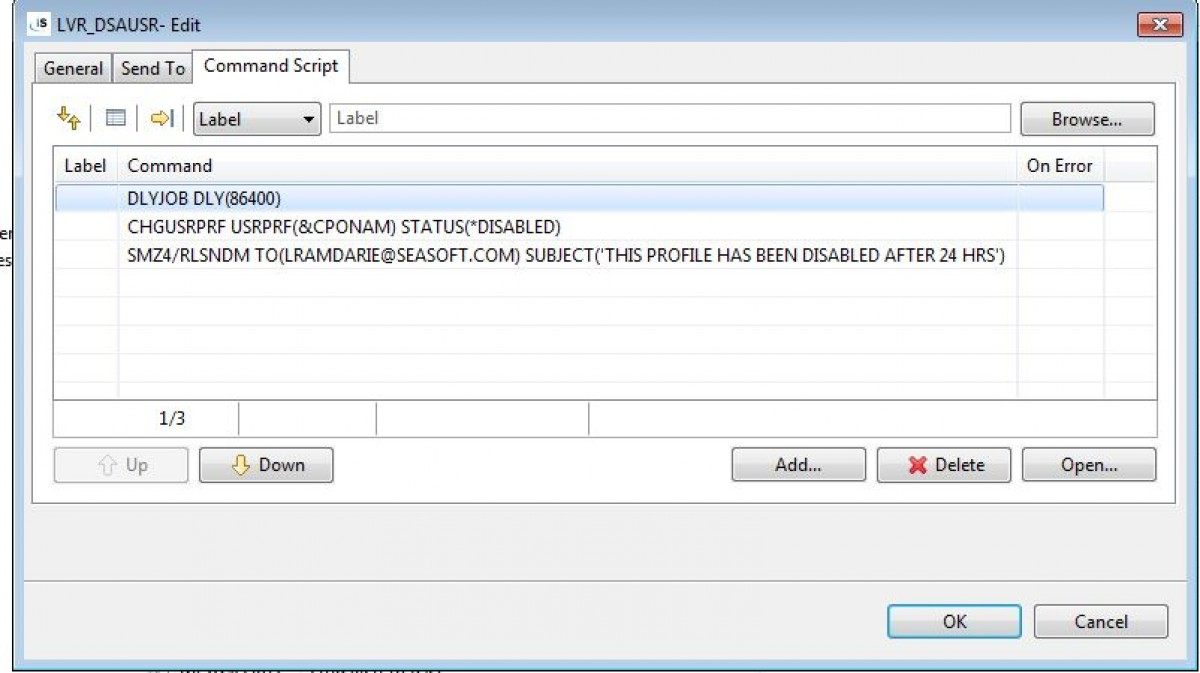
The CMS (Compliance Monitoring System) provides alerts, warnings and corrective actions to threats in real-time

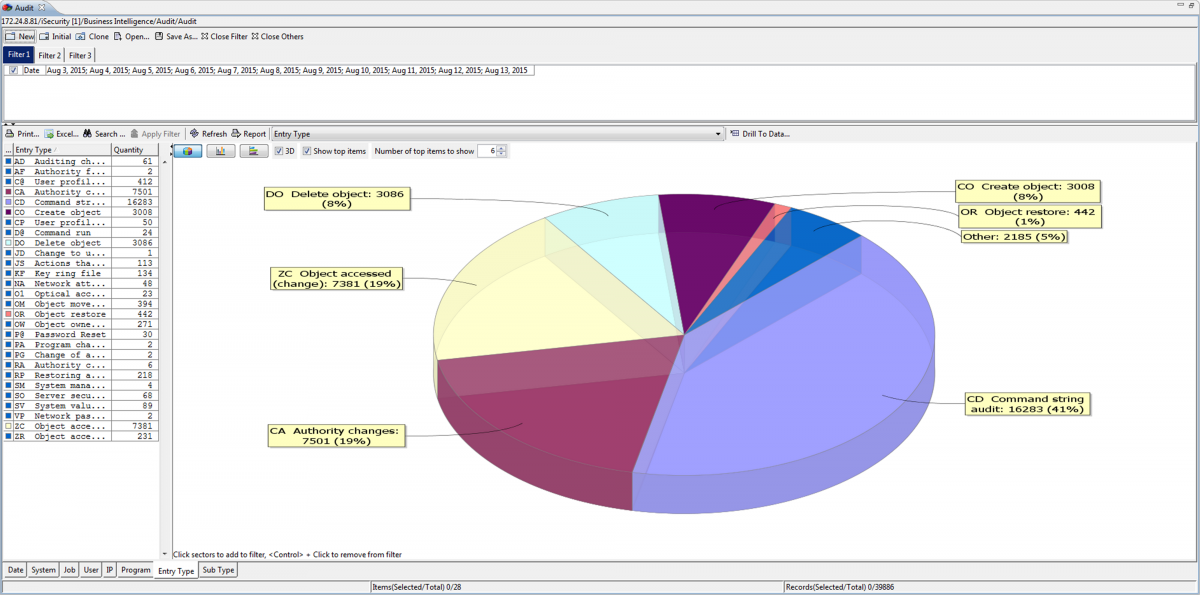
iSecurity Visualizer Business Intelligence System available for investigative analysis of IBM i security events.
 READ PRODUCT SHEET
READ PRODUCT SHEET