Cybersecurity and Compliance
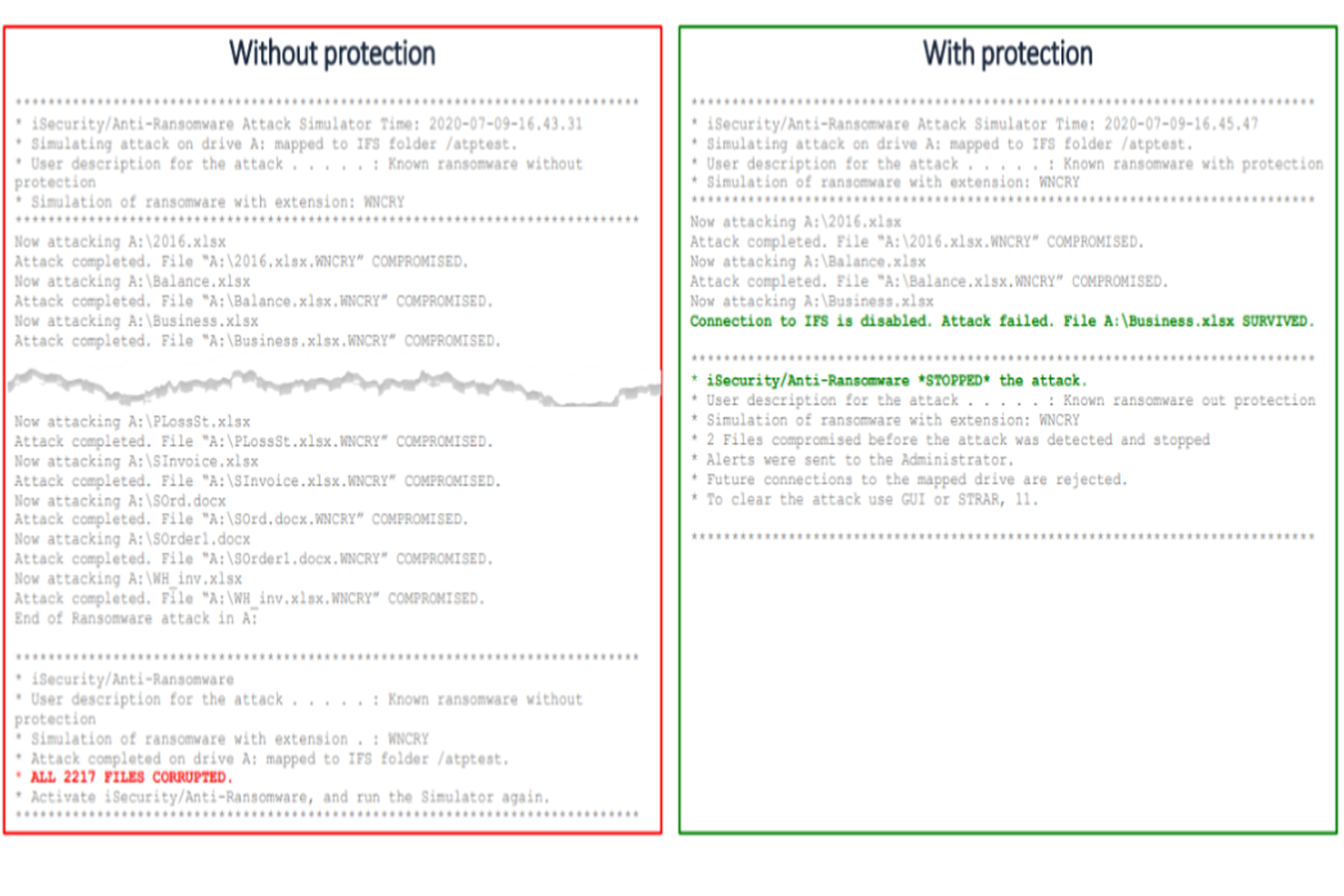
iSecurity Anti-Ransomware protects against ransomware attacks that infect and encrypt Integrated File System (IFS) files via mapped/shared drives.
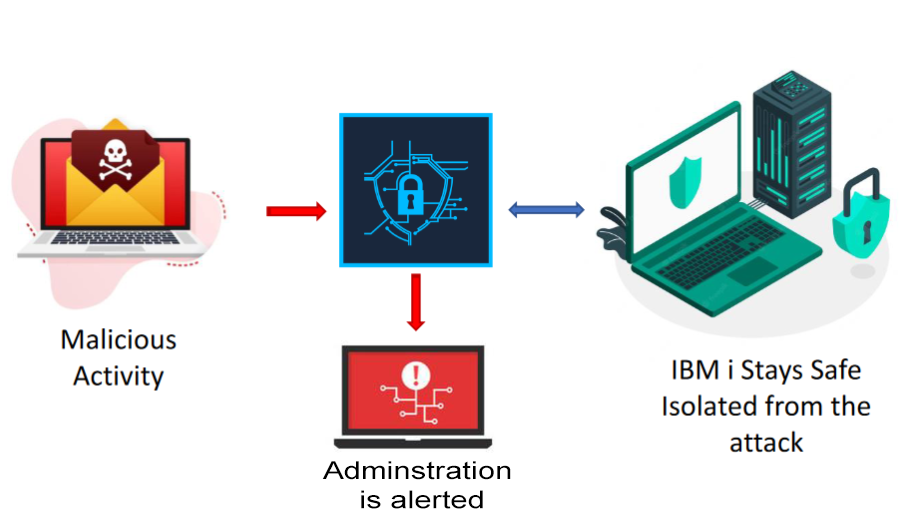
Anti-Ransomware helps to detect high-volume cyber threats deployed from external sources, helping to isolate the threat and prevent further damage to your environment.
iSecurity Anti-Ransomware is a proactive solution, designed to recognize and protect your IBM i servers quickly and efficiently from known and unknown (zero-day) threats, as soon as malicious activity is diagnosed.

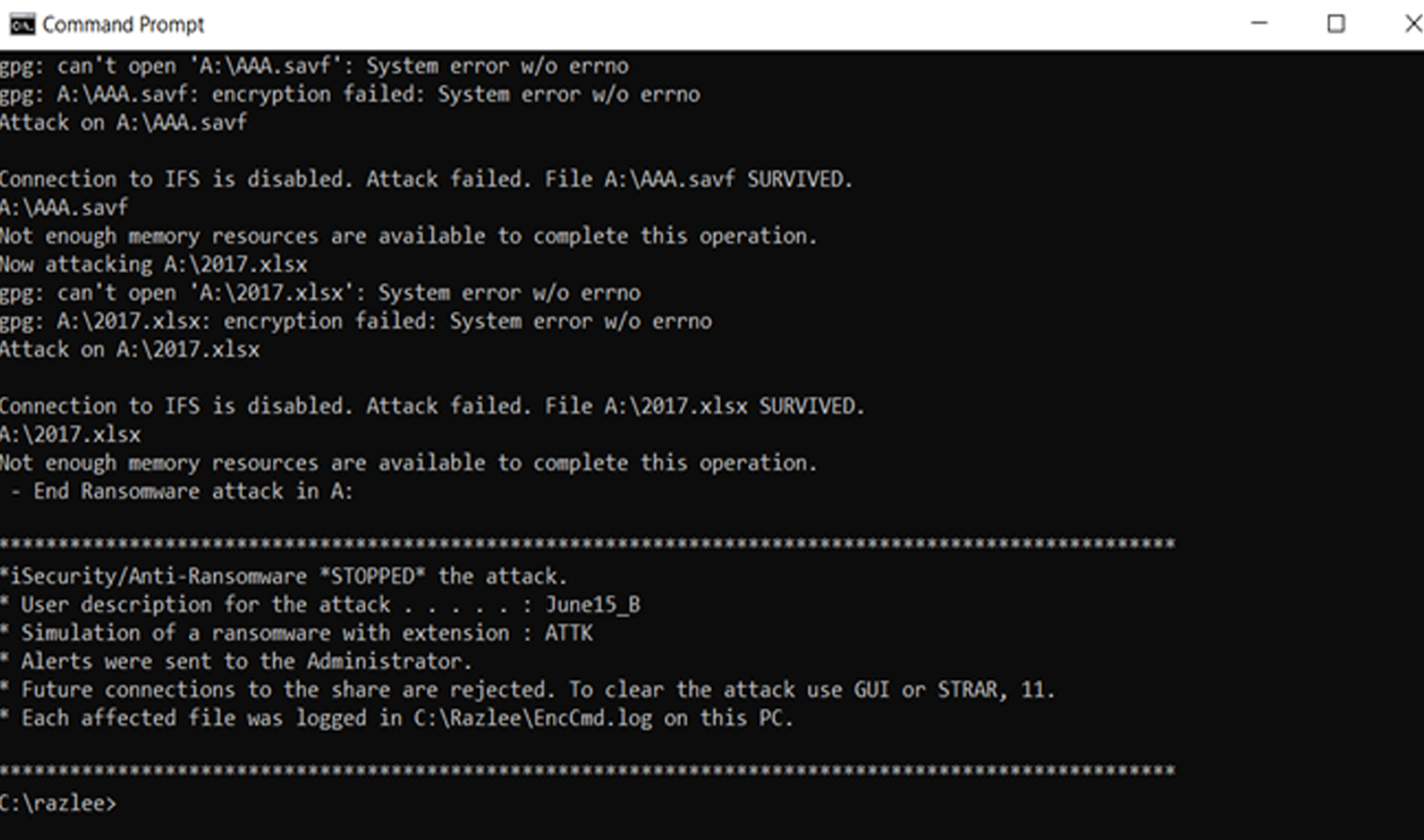
Identifies, delays, stops and reports on ransomware attacks in real-time

Uses multiple ransomware behavioral characteristics to detect suspicious activity

Detects only mode alerts you to possible suspicious activity while live mode alerts and counters attacks

Detects and disconnects remote devices performing suspicious activity, limiting damage inflicted in an attack

Provides real-time alerts and activity logging
 READ PRODUCT SHEET
READ PRODUCT SHEET