iSecurity Authority on Demand
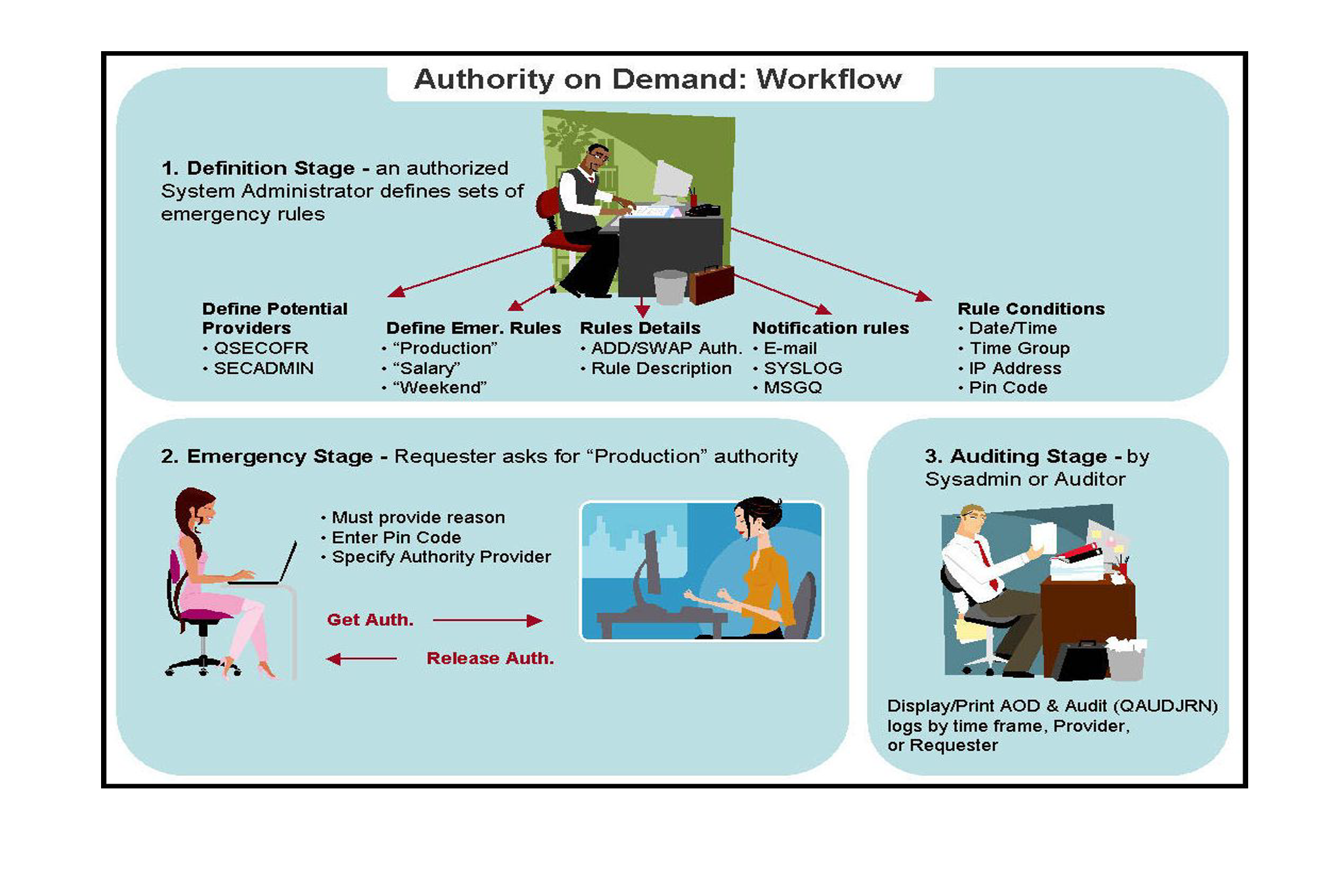
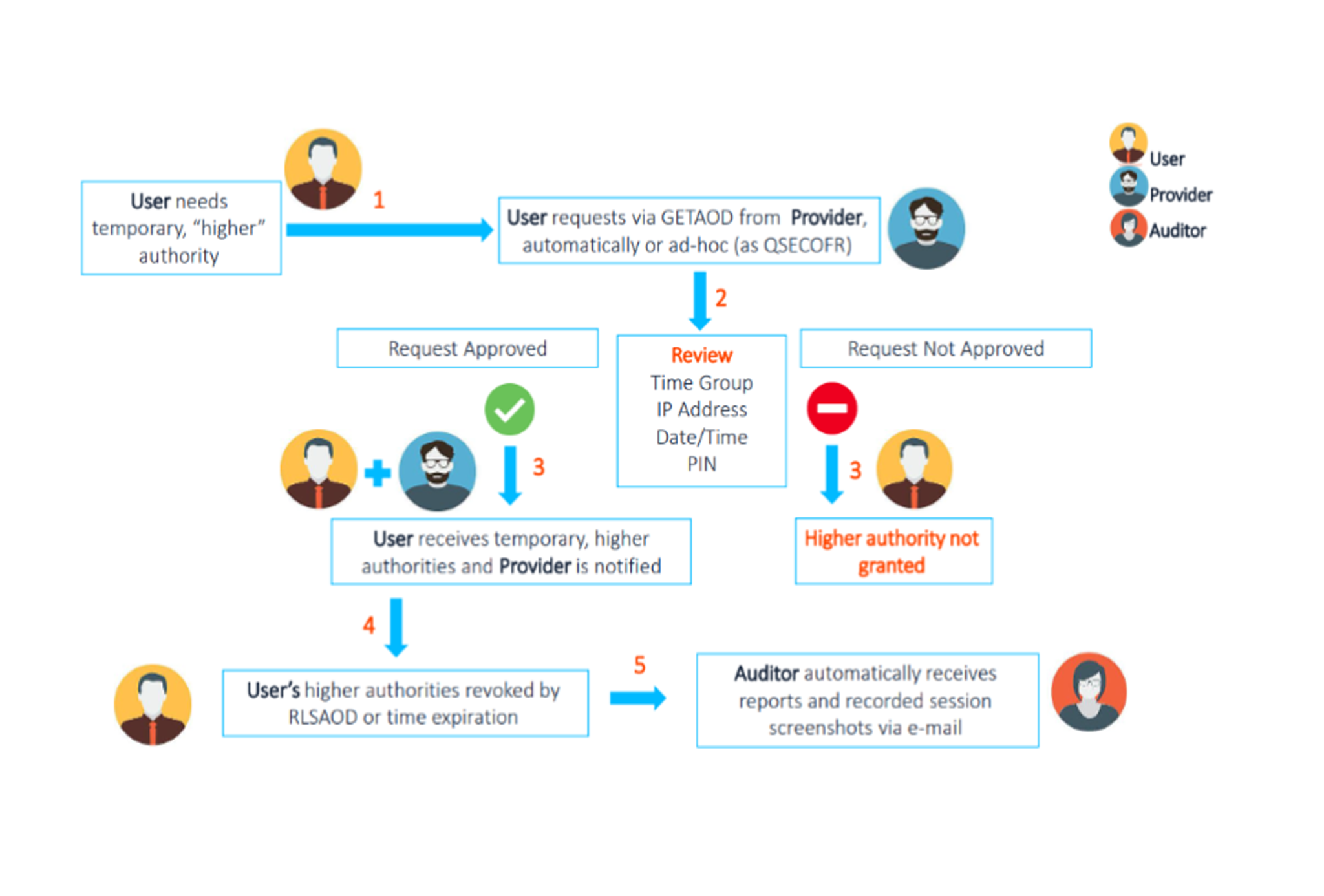
iSecurity Authority on Demand (AOD) provides an advanced solution for granting special authority access (including *QSECOFR authority) to critical application data, processes, and OS functions.
AOD gives administrators the ability to automate granting special authority and permissions on a temporary basis, when necessary.
With full audit and reporting capabilities, a historical record will always be available.
iSecurity’s Capture product can be added as an option to further enhance historical records with automated screen captures.

Automates granting special authority access to IBM i users, including audit trail records and documentation

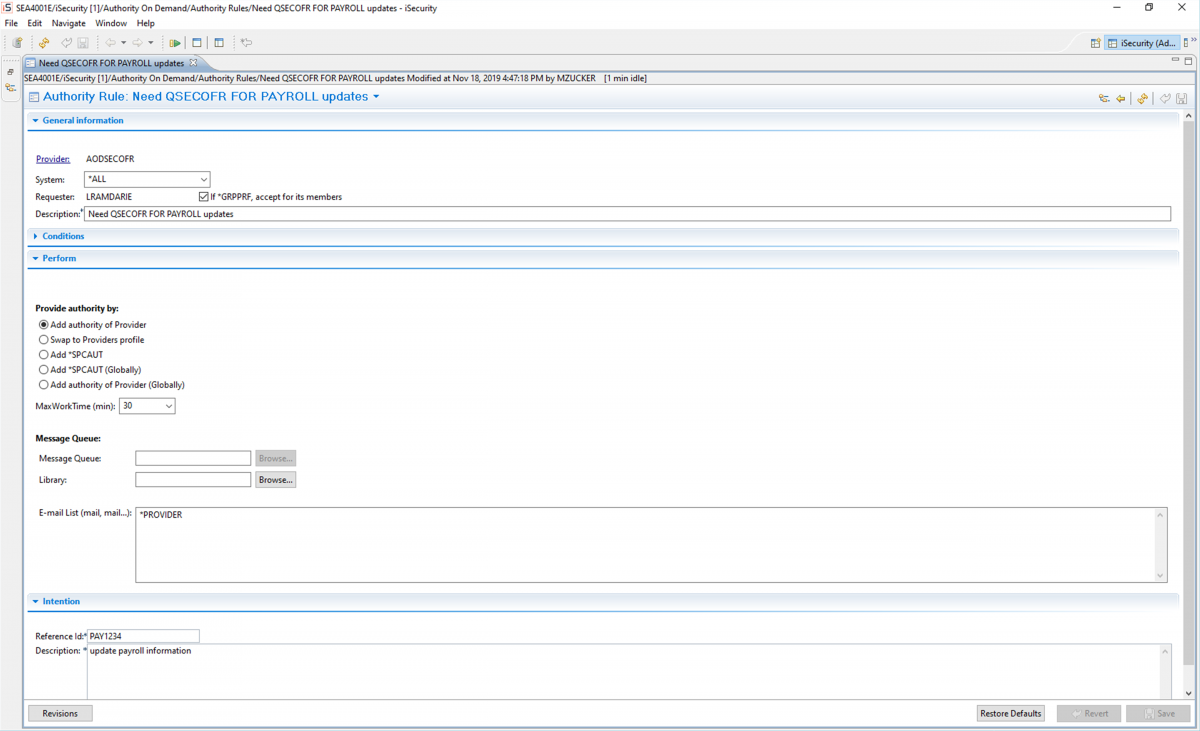
Users can request temporary access to pre-determined IBM i objects

Reduces Identity Access Management workload

Advanced auditing for change management

Reduces the need for multiple user accounts
 READ PRODUCT SHEET
READ PRODUCT SHEET