Part 1: Building Defense in Depth to Protect the IFS
This blog is the first in a series of posts that focus on IBM i Integrated File System (IFS) security and what can be done to protect your IBM i IFS against virus & ransomware cyberattacks.
Today’s blog focuses on:
- What is the IBM i IFS & how it is susceptible to virus & ransomware attacks
- How IFS cyberattacks occur
- What happens to your IBM i servers when a cyberattack occurs
- The five ways you can build an effective defense in depth strategy against IFS cyberattacks
This post is an overview of IFS cyberthreats and cyber protection, what a defense in depth strategy is and what security layers comprise an IBM i IFS defense in depth strategy. Part 2 (read here) presents a comprehensive view of the five layers of an IFS defense in depth strategy and techniques for implementing that strategy.
What is the IBM i IFS?
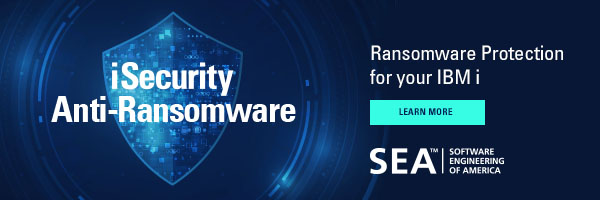
The Integrated File System (IFS) is a collection of logical file systems that i servers use to access different storage segments on an IBM i system. As shown in figure 1, the IFS is organized as a series of logical units that are shown as files, directories, libraries and objects.
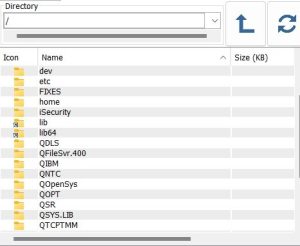
Figure 1: A typical IBM i IFS directory structure
Each file system has its own structures and rules for accessing the information in storage. The QSYS.LIB file system, for example, is the native IBM i library system, that contains all the system and application libraries along with other native objects on the system. Its objects are accessed through programs, commands and the operating system. The QOPT file system is the optical file system for accessing optical devices such as DVDs. The root (/) file system is at the top of the directory, and it is used for stream file storage. Root (/) can also be used to access the other file systems (ex., /QDLS, /QSYS.LIB, etc.).
Here is a list of some file systems contained or accessed through the IBM i IFS.
- root (/)
- Document Library Services (QDLS)
- File Server (QFileSvr.400)
- IBM i file server (QFileSvr.400)
- IBM i NetClient (QNTC)
- LAN Server/400 (QLANsrv)
- Library (QSYS.LIB)
- Network File System (NFS)
- Open Systems (QOpenSys)
- Optical Support (QOPT)
- User-defined file systems (UDFSs)
Anatomy of an IFS cyberattack
Even though ransomware and virus programs cannot natively run on the IBM i, the Integrated File System (IFS) can be a victim of a ransomware or virus cyberattack. Its files can be corrupted or encrypted just like files on a Windows or Linux server can get corrupted. Ransomware and virus attacks reach and corrupt IBM i objects through file shares and mapped drives. Let’s go through the story of a ransomware/virus cyberattack by looking at figure 2.
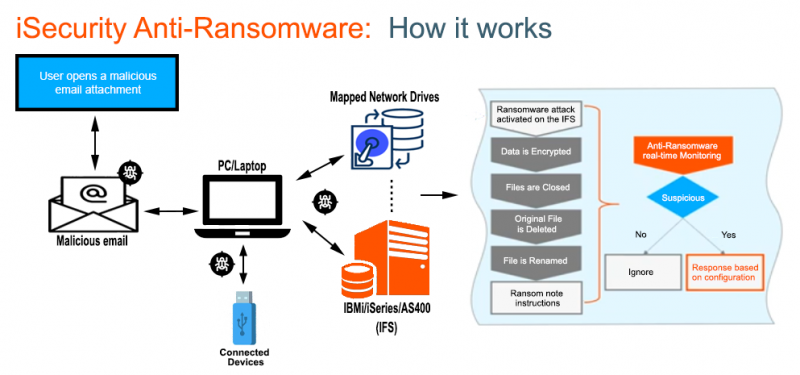
Figure 2: How viruses & ransomware attack IBM i IFS files
The PC/laptop shown in figure 2 has two sets of mapped network drives. The top set marked with a purple disk drive has its network drives mapped to a standard Windows/Linux file server. The bottom set of red mapped drives are mapped to locations in an IBM i Integrated File System folder like the ones shown in figure 1. For this example, let’s say the IBM i drives are mapped to the /home folder off the root (/) file system in the IFS shown in figure 1, and the signed-on user has all authority (*ALL) to the files in the /home folder.
One day, our PC/laptop user receives a malicious email. The user clicks on one of the email links and a ransomware/virus program is downloaded to their computer. The user might have also click on a bad URL off a website or inserted an infected storage device such as a USB drive into their laptop. In all three cases, our user’s laptop is now infected by a ransomware/virus program that is now running live on their device.
Once active, the ransomware/virus program starts looking for other machines to infect. It looks at all its connected mapped drives and it spreads the infection to and corrupts files in those drives. Any IFS folders that the signed-on user has read, write and update authority to will be infected.
If the attached PC is infected with ransomware, files in the connected IFS folder will also be renamed and encrypted (as shown in the rightmost column of figure 2). A ransom note with instructions on how to pay the ransom and obtain a de-encryption key, will be left on one of the infected IFS drives.
In other instances, viruses/ransomware can also be spread to IFS files through local, cloud and Internet-based utilities & applications such as FTP and SQL, among others.
And that is how easy it is to infect IBM i IFS files with viruses or ransomware.
What happens when my IFS is attacked?
The practical effects of virus & ransomware attacks are shown in figure 3. IBM i applications that rely on IFS files can stop working, data can become corrupted, and company information can be exposed & stolen. An attacking program can also leave copies of itself in an IFS folder that can be downloaded and infect other devices, propagating the attack.
| Issue after IFS cyberattack occurs | Examples |
|---|---|
| Stream files used for application support are corrupted | IBM i applications with corrupt files stop working including Java/UNIX apps, web serving, open-source applications, VB scripts, and faxing. |
| Corrupted IFS-based databases | Frequently updated data and imported data from other systems is encrypted and renamed |
| User files corruption | Spreadsheets, reports, Word docs, graphics, company docs, warranties are corrupted or encrypted/renamed |
| Exposed and stolen IFS files | Attackers steal information and demand ransom not to publish |
| IBM IFS becomes a virus & ransomware source | Ransomware & virus programs can be stored in the IFS and infect user machines on downloads |
Figure 3: What happens when IFS files are infected?
Defense in Depth Protection Against Virus & Ransomware Attacks
How do you protect your IBM i IFS against viruses & ransomware? SEA recommends creating a defense in depth strategy to help protect against IFS cyberattacks.
Similar to defending a medieval castle against marauders, where the castle was protected by moats, drawbridges, archers in towers, etc., defense in depth strategies deploy multiple layers of security controls to protect against cyberattacks. Multiple security controls provide redundancy when defending the IFS. If one security control fails, another control can step in to provide continual IFS protection.
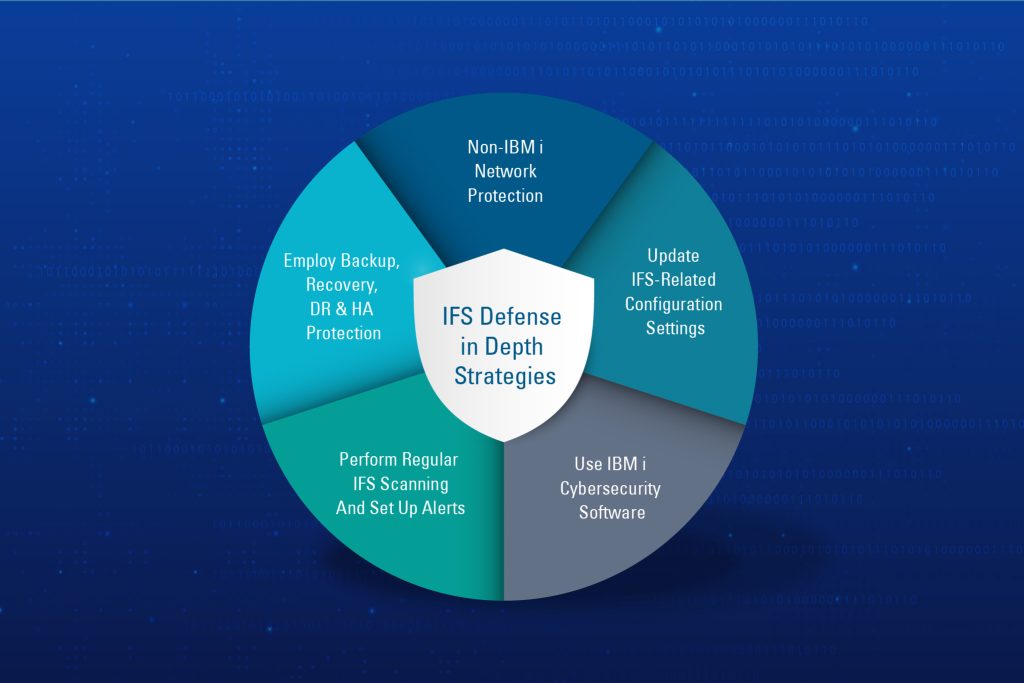
Figure 4: Five security layers for an IFS defense in depth strategy
For IFS defense in depth, figure 4 shows the five security layers you can implement that will defend against IFS cyberattacks. These security layers are:
- Non-IBM i network protection involves securing network and compute devices against virus and ransomware. Anything that touches the IBM i should have anti-virus/anti-ransomware software installed, especially if the device is mapping network drives to the IFS.
- Update IFS-related Configuration Settings: There are a number of native IBM i configurations that administrators can make to secure the IFS against unauthorized access & modification. For instance, it is not best practice to make ‘/root’ a public share as it would allow anyone to create a mapped drive to the entire IFS.
- Use IBM i cybersecurity software: There are several third-party IBM i security packages available including many packages from SEA that protect against viruses, ransomware and unauthorized access.
- Perform regular IFS scanning and set up alerts: Employ scheduled batch IFS scanning to search for infected objects and perform on-demand scanning that scan files as they are opened or closed on the IFS. Once infections are detected, appropriate automated responses can be employed, and IBM i emergency responders can be notified.
- Employ Backup, Recovery, DR & HA protection: Ensure you have a regular backup schedule and make sure you regularly test your recovery routines. Protect other auxiliary IBM i partitions in addition to your production partitions.
These layers form the outline of your IBM i IFS security plan. Join us in the coming weeks for the next blog post in this series where we’ll specifically show how to implement this plan to provide IFS peace of mind.