
iSecurity Anti-Ransomware protects your Integrated File System (IFS) files from PC-based ransomware attacks. It uses real-time ransomware detection and disablement, IFS directory scanning, continually updated ransomware signature files, and honeypots to stop IBM i ransomware attacks.
Although ransomware cannot be directly executed on an IBM I, it can affect IBM i Integrated File System (IFS) folders by encrypting and renaming files (see our sidebar How Ransomware attacks IBM i files for more information). Encrypting IFS files can disable IBM i applications that use stream files in their processing, including i applications such as document management, email, EDI, Web serving, and other apps. It can also destroy user files—such as Word, Excel, and PDF files—that are stored on the IFS.
Here’s how iSecurity Anti-Ransomware works and why you should look at it to protect your shop from ransomware.
How iSecurity Anti-Ransomware works
Figure 1 shows how iSecurity AR fights ransomware attacks on your IFS.
A PC user creates a mapped drive to the IFS. The user clicks on a malicious e-mail that kicks off a ransomware program on the PC. The ransomware starts encrypting files on all of its mapped drives, including IFS mapped drives. iSecurity AR detects the attack, and responds in three ways, according to how it is configured.
- Stopping the attack—iSecurity AR disconnects and blocks the IP connection between the infected PC and the IFS, immediately stopping the attack. Blocked IP addresses will be unable to map a network drive until they are removed from iSecurity AR. The software can also be configured to automatically shut down the IBM i NetServer server to stop all IFS file sharing in case other PCs are infected.
- Alerting responders—iSecurity AR sends notices out to all designated IT responders that an attack has been detected on the system. Alerts are sent out via email or as messages to the system operator console (QSYSOPR).
- Performing additional actions—The product can automatically shut down the PC generating the ransomware attack (requires PC configuration) and then call a user-written IBM i remediation program.
Ransomware signature files are updated daily, ensuring that the software is always scanning for the most current ransomware releases. For zero-day ransomware releases (new code that has not been identified yet), the software has a matching algorithm designed to detect unknown and newly released versions.
iSecurity AR allows you to exclude IFS objects from its scanning, excluding files and folders that may produce false positives or that are not accessible from IFS file shares.
The package also contains attack simulator software that allows you to obtain information about your IFS setup. Details on any real or simulated attacks can be saved in a log file. Log file information can be used to set up iSecurity AR configuration settings for triggering anti-ransomware actions. iSecurity AR log files give you information on every object iSecurity AR touched during its scans, plus IBM i audit journal data (QAUDJRN).
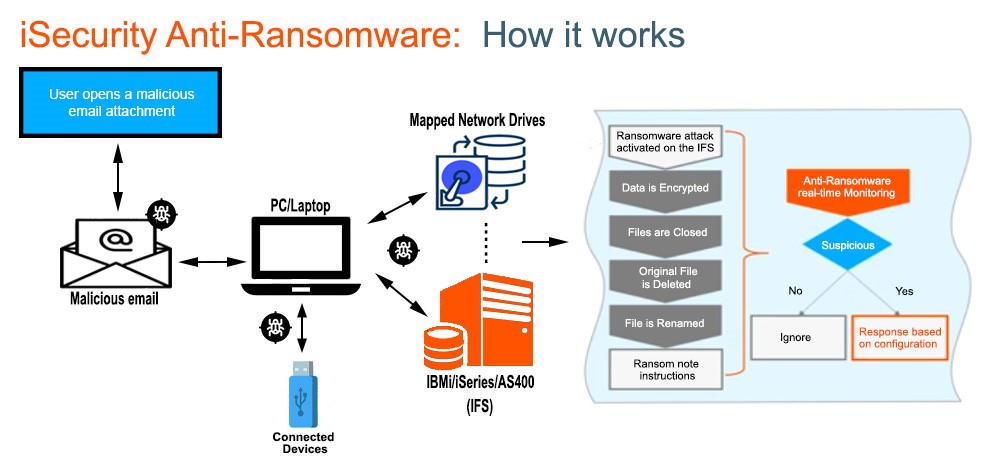
Figure 1: How iSecurity Anti-Ransomware works
The Method of Detecting a Duck…and Ransomware
An old cliché states that “If it looks like a duck, swims like a duck, and quacks like a duck, then it probably is a duck.” This same Method of Detecting a Duck also works for detecting ransomware as it is attacking IFS files (“If it looks like ransomware….”). iSecurity AR uses these monitoring and assessment methods to detect and stop an attack.
- Continually running IBM i ransomware detection servers that scan IFS folders, and scan individual files when an IFS object is changed.
- Looking for a specific order of activities associated with ransomware. If the servers see a pattern or behavior showing suspicious activity—such as when files are continually being copied, encrypted, renamed, and then the original file is deleted–it may conclude a ransomware attack is occurring.
- Checking IFS file extensions listed in downloaded ransomware signature files, looking for matches.
- Checking for unusual and unexpected IFS file changes.
- Searching for Zero-Day (unknown) ransomware variants, based on other indicators coded in iSecurity AR algorithms.
- Monitoring files in IFS honeypot folders, looking for ransomware modifications. A honeypot is an IFS folder that is loaded with important looking but worthless files. The honeypot is configured to be attacked first before any production file folders, giving iSecurity AR time to react to the attack in progress. Given the delay provided by the honeypot attack, iSecurity AR can stop the attack before it affects production IFS files.
- iSecurity AR also includes Support Object Integrity Control to ensure your IBM i License Internal Code (LIC) has not been damaged or corrupted. This feature runs an IBM i API that checks the LIC. Object integrity control is usually only available at IPL. iSecurity AR can perform LIC checking as part of its normal scanning process.
Good hygiene leads to a clean machine—Other ways to protect against ransomware
To further protect against ransomware and other viruses hitting your IFS, we also recommend you make the following changes, in addition to installing iSecurity AR.
- Be selfish with IFS file shares—Review all your file shares. Consolidate and remove any shares that are no longer used. Only provide file share access to authorized users. The fewer file shares and authorized users you have, the fewer chances for IFS ransomware encryption.
- Never map the IFS root (/) folder to a file share—PC network drives mapped to root (/) can be used to reach and encrypt any object on an IBM i server. There have been some recent reports of ransomware encrypting files in the QSYS.LIB file system (native IBM i objects), using an *ALLOBJ user profile in an extremely unsecured system. QSYS.LIB can be reached from a PC file share if you assign the root (/) folder to a file share. Delete and replace any IBM i file shares that provide access to the root (/) folder.
- Be stingy with *ALLOBJ authority—Users who start a NetServer file share with all object (*ALLOBJ) authority will be authorized to change, rename, and delete IFS files, if their PCs become infected with ransomware. Limit *ALLOBJ users as much as possible. Encourage your admin profiles to use a non-security officer profile when mapping drives to the IFS.
- Maintain a daily IFS backup—Back up your full IFS once a day, or more if you are able to. If you have implemented Flash Copy, use that to take IFS backups. If the IFS falls victim to ransomware, you will probably need to restore files from the latest backup you can find. Any changes you cannot restore will be lost in a ransomware attack, so take frequent daily backups of your non-QSYS.LIB IFS.
- If you fall victim to ransomware, DO NOT PAY THE RANSOM—FBI research says that 70% of those who pay ransom end up losing their money, their data, or both. Rely on regular daily backups and IFS restores to reverse ransomware infections.
Shoring up the war against malware
iSecurity Anti-Ransomware is a critical package for any organization that exposes its IFS via Windows mapped drives. Similar to SEA’s other anti-malware product, iSecurity Anti-Virus, it protects IFS files from external threats caused by exposure to Windows PCs. It can also be valuable in regulatory environments where Advanced Threat Protection is required.
iSecurity Anti-Ransomware is now available from SEA. Please contact us for more information or if you would like a demonstration.
Sidebar: How Ransomware Attacks IBM i Files
Using IBM i NetServer file shares, Windows PCs access Integrated File System folders as mapped drives, allowing users to read, write, modify, or delete Integrated File System (IFS) data.
Ransomware-infected PCs encrypt and rename IFS files through NetServer mapped drives, making them unusable to IBM i applications and storing ransomware programs directly on the IFS.
Ransomware attackers announce themselves after activation and post instructions to pay a ransom in bitcoin to decrypt and rename your IFS files.
Organizations have three choices when their IFS files are infected with ransomware.
- Pay the ransomware. Even with paying the attacker, you may never get a decryption key, receive a decryption key that does not work, or receive a decryption key that stores a different ransomware or virus program on your PCs or the IFS. According to the 2019 Cyberedge Group Cyberthreat Defense Report,45% of ransomware victims paid their attackers last year but only three out of five firms that paid the ransom successfully recovered their data.
- Restore any encrypted IFS files from a recent backup. A time-consuming solution and you lose any new IFS files or changes that occurred since the last backup.
- Stop ransomware attacks before they start by installing an IBM i anti-ransomware program, such as iSecurity Anti-Ransomware. Anti-ransomware programs can stop ransomware attacks in real-time, as they are occurring. Anti-ransomware programs can prevent almost all damage from an attack. When minor damage does occur, it can be mitigated by a honeypot strategy.





