
Today’s blog looks at how IBM i password security policies are created by using password requirements that are implemented through password controls/system values. We’ll look at how security policies are built up requirement by requirement, how they are implemented in controls and some of the more common IBM i password requirements and controls.
Password Security Policies, Requirements and Controls
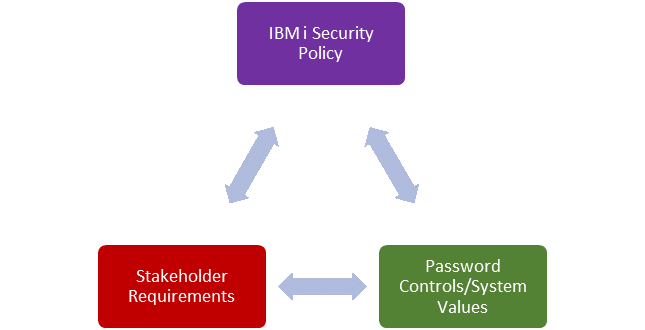
An IBM i password security policy is the sum total of all implemented password requirements specified by internal and external stakeholders. Password requirements are implemented by IBM i password controls as system values.
As shown in figure 1, each element feeds into and affects the other two elements with the driving force being stakeholder requirements: the policies and controls you must implement to secure your IBM i.
Password requirements
Password requirements are specified by security stakeholders. They can include IBM i-based requirements such as minimum password lengths, how often passwords should be changed, number of digits and upper- & lowercase characters, etc. Table 1 shows several examples of common IBM i password requirements.
Password requirements define how password security must be enforced on your system. They generally fall into four password requirement categories:
- Password strength—Rules for creating complex passwords that are difficult to guess or crack
- Password expiration—How often a user must change their password
- Password changes—How often passwords can be changed
- Password re-use –Rules governing how new passwords must be different from previous passwords
Password requirements can be defined by many different security stakeholders and sources, including:
- Enterprise security teams
- Organizational password security requirements
- Internal and external auditors
- Customer requirements and audits
- Regulatory requirements, including SOX, PCI DSS, GDPR, HIPAA
- Governmental agencies
- Best practices for passwords/passphrases, including National Institute for Security & Technology (NIST) guidelines
When changing IBM i password security policies, organizations usually reference password requirements from all interested stakeholders, merge them into a consolidated requirements list and implement them using IBM i password controls.
In some instances, different security stakeholders may specify different password requirements. This can occur when a regulatory body may specify minimum password lengths of six characters while another stakeholder may specify minimum password lengths of seven characters. In cases where password requirements conflict, it is generally (but not always) best to go with the stricter requirement.
Password controls: Turning password requirements into password security policies
Password requirements are implemented using IBM i password controls. For IBM i systems, password controls are typically configured as system values. Password controls can be modified using Navigator for IBM i (Navigator) or 5250 commands.
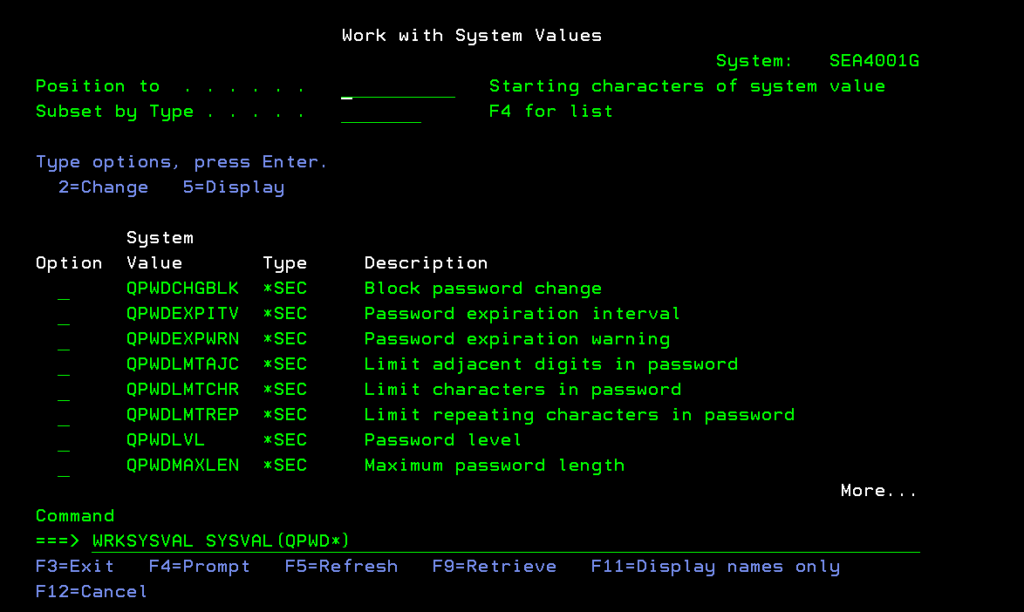
Individual password controls can be configured as system values on the green screen by using either the Work with System Values (WRKSYSVAL) command or the Change System Value (CHGSYSVAL) command. You can display and work with all IBM i password control system values by entering the WRKSYSVAL command using either *QPWD or *SEC in the System Value (SYSVAL) parameter, like this:
WRKSYSVAL SYSVAL(QPWD*) or WRKSYSVAL SYSVAL(*SEC)
Either command will produce a list of password control values that you can display or change, shown in figure 2:
You can also set password controls in Navigator for IBM i by using the Configuration and Service->System Values: Password path, as shown in figure 3.
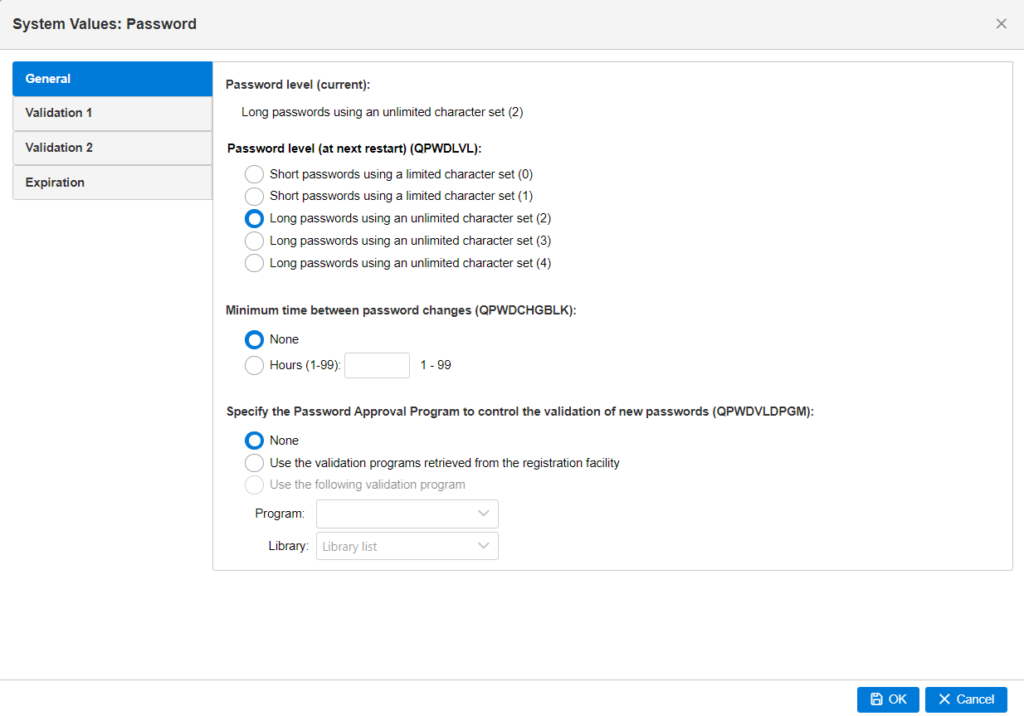
Using Navigator for password control configuration allows you to configure groups of controls in tandem with each other. Whereas using the WRKSYSVAL or CHGSYSVAL commands generally only allows you to configure IBM i password controls individually.
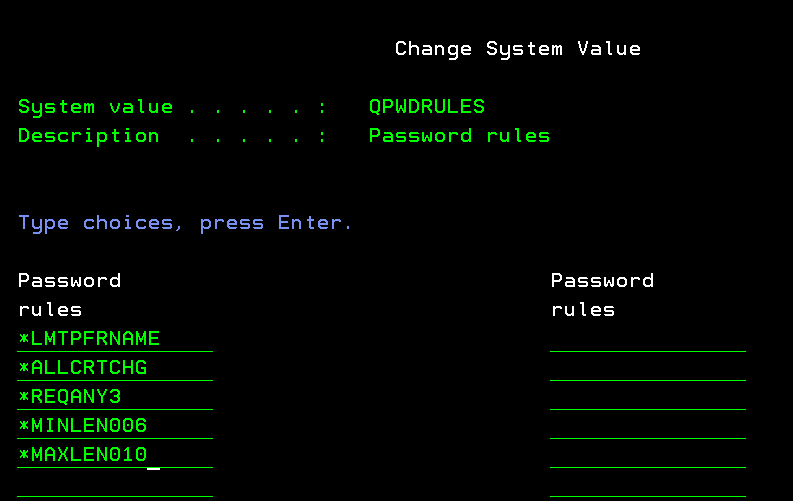
Password controls can also be configured in tandem by adding literals to the Password Rules system value (QPWDRULES). Adding password-based literals to QPWDRULES activates several password controls in one green-screen configuration, allowing you to see most of your password controls on one screen, as shown in figure 4.
Common IBM i password requirements & how to set them
Table 1 lists some of the more common password requirements and how to set them up as IBM i password controls. Note that this is not an exhaustive list of all possible password requirements/controls, only some of the more common configurations.
Password control settings in Table 1 are displayed showing the values to change in Navigator for IBM i or 5250 commands. When a control can be set by adding a literal to QPWDRULES, configuration instructions for Navigator for IBM i and the QPWDRULES system value are both shown.

The Fundamentals of IBM i password security
Taken together, these items provide a fundamental overview of how IBM i password security policies work and the basics of creating them. Please contact SEA if you’re interested in learning more about IBM i password security.





