
The IBM i security audit journal (QAUDJRN) collects all security events occurring on an IBM i system. Unfortunately, IBM provides few tools for reporting from that data and there’s a lot of critical security event information that QAUDJRN doesn’t collect. Most shops have to produce DIY systems or use SQL to report on QAUDJRN activity.
That’s where SEA iSecurity Audit comes in. iSecurity Audit provides over 200 reports using QAUDJRN and other object security data that produce the insights and mandatory reporting your organization needs. Here’s a quick look at how iSecurity Audit produces all the IBM i security reports you wish you had.
iSecurity Audit offers both static and dynamic reporting
QAUDJRN collects security events as journal entries for all types of issues. Each entry is coded with a two-digit entry type. You can check out all the different IBM i security event entries that QAUDJRN collects by clicking here.
iSecurity Audit uses its powerful query and report generation capabilities to create two different types of security auditing reports over QAUDJRN and other security data.
- Static reports—Reports that describe information about objects, their attributes, and values, such as displaying all users who didn’t sign on for the last 30 days, users with default passwords, or all your system values. Information that comes from objects is at rest and doesn’t change very often, which is why these reports as considered static.
- Dynamic reports—Reports that show the real-time status of a security event, such as when someone changed a system value, had a login failure, or used a command line. These reports use QAUDJRN audit information to show the history of a security event. QAUDJRN information is recorded as the event happens, it’s always changing, which is why we refer to these reports as dynamic. Dynamic reports may also include bundled QAUDJRN information, where information from several audit entry types can be included in a report.
Both types of reports are frequently requested by regulatory auditors. For some iSecurity Audit reports, dynamic QAUDJRN information can be combined with static object information–including user profile, object information, and system values–to extract more meaningful information about your current security configuration.
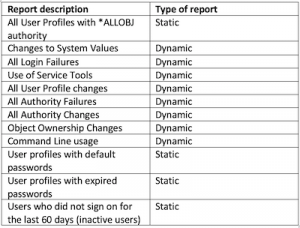
Table 1: The most commonly used static and dynamic reports in iSecurity Audit
Table 1 shows the most commonly used iSecurity Audit reports, and whether each report is a static or dynamic report.
By offering static, dynamic, and combined security reporting, iSecurity Audit can answer the three big questions auditors and management ask when dealing with security data:
- What is the current state of your IBM objects and their security? (Static reporting)
- What security events happened, and when and how did they happen? (Dynamic reporting)
- What security holes are still out there that haven’t been addressed? (Static and dynamic reporting)
Adding new reports to iSecurity Audit
All current iSecurity Audit reports were specially created from customer requests. SEA frequently adds to its product capabilities when a customer has a valid need, and expects to continue doing so in the future.
How iSecurity Audit reports are generated
iSecurity Audit reports are always generated with current security information. Reports can be generated on a schedule or run on demand. Reports can also contain summary and explanation pages to explain why the reports were requested and any other relevant information not included in the data. Audit reports can be viewed online. They can also be emailed as PDFs or in other formats, such as Excel spreadsheets.
Using Audit reports for operational purposes
iSecurity audit reports can also serve as operational tools. You can set up a baseline for your system values, for example, and instruct iSecurity Audit to alert IT Ops personnel when there’s a deviation from that baseline. This feature enables the package to proactively warn users when an auditing or compliance issue occurs. Note: if you baseline your system values, we recommend you exclude any date and time system values from your baseline, as they can correctly change automatically according to your IBM i configuration.
For more information
iSecurity Audit reports are incredibly flexible. They take the trouble out of creating management and auditing reports. Please feel free to contact us at SEA software if you want to learn more about how these products can help your shop fill its own security reporting requirements.




