
Default passwords are IBM i user passwords where the password value is equal to the user ID. One example would be a user ID named SEASOFT who has a password value of SEASOFT. Needless to say, default passwords are dangerous because bad actors and hackers can discover and use them to easily access IBM i systems.
Fortunately, IBM i provides several options for preventing, detecting, expiring and mitigating default passwords. Here is SEA’s five-step process for stopping default password usage for IBM i users.
Step 1: Update to IBM i 7.5
In i 7.4 and below, the default password value for new user creation was *USRPRF, which meant that if no other password was entered, the password for a new user would be set to the user profile name. If we create a new user named SEASOFT under i 7.4, for example, its default password would also be SEASOFT unless we changed it to something else.
In i 7.5, the default password value for a new user is *NONE. This means that if no unique password is assigned to a new user, that user will not be able to sign on to your IBM i system until a password is explicitly assigned. And fewer IBM i default passwords will be created.
The result is that you can reduce the number of default passwords on your system just by running IBM i 7.5.
Step #2: Stop users and administrators from creating default passwords
The simplest way to prevent default passwords from being used is to prohibit their creation. To do this, consider setting the following system password validation settings to stop administrators or users from creating default passwords. The system values shown in table 1 can be set by using 5250 green-screen commands (figure 1) or by setting Navigator for IBM i password controls.
| Default Password Validation System Value Control | Purpose of Password Control | Green-screen password control | Navigator for IBM i password control to set |
| User profile name cannot be used as part of user password. | Prevents user profile name from being used inside an IBM i password | Add the *LTMPRFNAME literal to the Password Rules (QPWDRULES) system value | Select the Restrict user profile in password setting from the System Values: Password Navigator path |
| Enforce all password validation options when creating or changing a password when using the Create User Profile (CRTUSRPRF) or the Change User Profile (CHGUSRPRF) commands | Prevents security officers and administrators from overriding the user profile name restriction when creating or changing a user profile password with CRTUSRPRF or CHGUSRPRF | Add the *ALLCRTCHG literal to the Password Rules (QPWDRULES) system values | Select the Enforce all password validation options when creating or changing a password with CRTUSRPRF or CHGUSRPRF setting from the System Values: Password Navigator path |
Table 1: Green-screen & Navigator for IBM i password controls to reduce default passwords
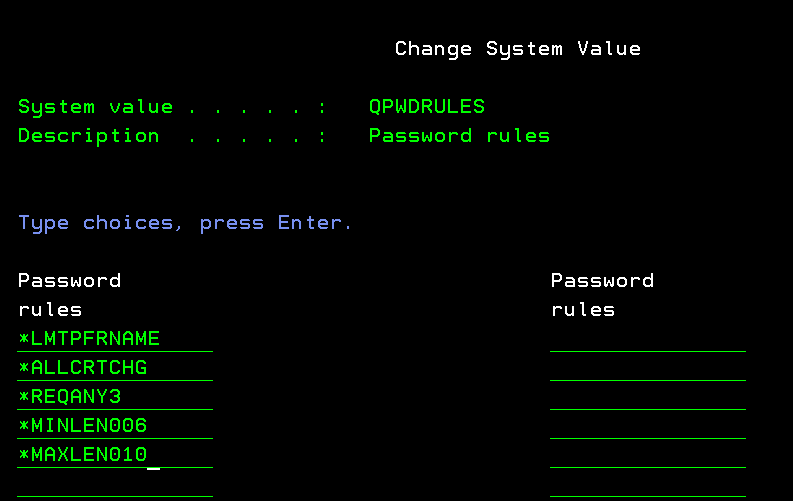
Figure 1: Add the *LTMPRFNAME & *ALLCRTCHG values to your password rules list to prevent default password rule creation
Step 3: Disable/Expire Existing IBM i Default Passwords
While previous steps prevent new default passwords from being created, the next step helps you detect and disable/expire any current IBM i users who have default passwords. You can create a list of default password users by using the Analyze Default Passwords (ANZDFTPWD) command, like this:
ANZDFTPWD ACTION(*NONE)
Which will produce a list of all IBM i users that have default passwords, similar to the listing shown in figure 2:
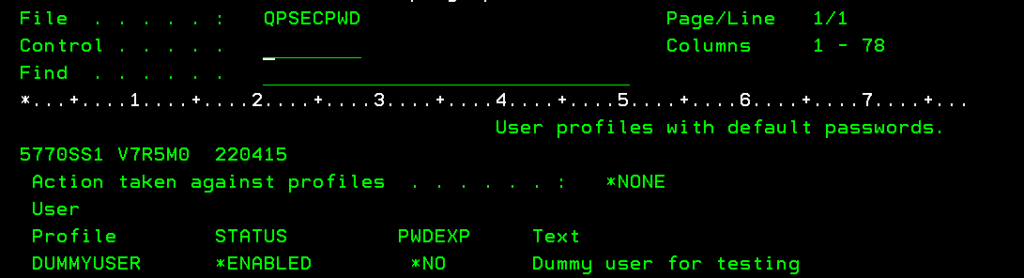
Figure 2: A sample ANZDFTPWD list
The ANZDFTPWD list will display any user that has a default password and whether their password is expired or active (the PWDEXP column). Auditors will frequently request you to run ANZDFTPWD to produce a list of default user passwords when auditing your system.
You can expire all default passwords or disable users with default passwords by modifying and running the ANZDFTPWD command with these parameters:
- To expire all users with default passwords and force them to change their passwords the next time they login, run ANZDFTPWD with the *PWDEXP value in the Action taken against profiles (ACTION) parameter:
ANZDFTPWD ACTION(*PWDEXP)
- To disable all users with default passwords (they can no longer sign on to the system), run ANZDFTPWD with the *DISABLE value in the Action taken against profiles (ACTION) parameter:
ANZDFTPWD ACTION(*DISABLE)
You can also expire, disable or change individual default user passwords by using the Change User Profile (CHGUSRPRF) command.
Once you’ve dealt with your existing users that have default passwords, you can run the ANZDFTPWD command one more time to produce an audit list that proves you’ve addressed all default password usage.
Step 4: Don’t forget your other default passwords: Dedicated Service Tools
In IBM i 7.4 & below, there are four system-provided Dedicated Service Tools (DST) users who are shipped with default passwords. In IBM i 7.5, IBM reduced that number to two users as shown in table 2.
| DST Level User ID | i 7.4 DST User | i 7.5 DST User | Default Password | Additional info |
| Basic Capability | 11111111 | — | 11111111 | No longer available in i 7.5 |
| Full Capability | 22222222 | — | 22222222 | No longer available in i 7.5. This user password does not expire after first usage. |
| Security | QSECOFR | QSECOFR | QSECOFR | Security user password expires the first time it is used |
| Service Capability | QSRV | QSRV | QSRV | Service tool user password expires the first time it is used |
Table 2: IBM Dedicated Service Tools users with default passwords
Consider changing these passwords to avoid problems with unauthorized users accessing service functions. If the changed passwords are forgotten, IBM has a published procedure to reset the QSECOFR password to its default value, which then can be used to reset the other DST passwords.
Step 5: Using Multi-Factor Authentication to mitigate default password usage
When you implement an IBM i Multi-Factor Authentication (MFA) solution, you may also invoke partial protection against unauthorized IBM i default password usage. Because MFA requires two authentication factors for a valid login, if a bad actor or hacker discovers a default password (Knowledge MFA factor), they will not be able to fully sign on to an IBM i system unless they also discover the user’s second authentication factor.
In this regard, MFA can help stop unauthorized default password usage. However, keep in mind that it is possible to steal or phish two MFA authentication factors (see What is Phishing-Resistant Multi-Factor Authentication?) so MFA user login security can be defeated. And remember that MFA will be no protection for default password users who are exempt from MFA requirements.
But it is worth mentioning that MFA can provide limited additional protection against unauthorized default password usage for MFA users.







