
New Federal cybersecurity standards and objectives to be met by end of FY 2024
If you’re a United States federal agency or dealing with a federal agency, you may be aware of the US government’s Federal zero trust architecture (ZTA) strategy to improve cybersecurity. The ZTA strategy requires governmental agencies to meet specific cybersecurity standards and objectives by the end of Fiscal Year 2024, Monday, September 30th, 2024.
How Federal ZTA originated
In May 2021, President Biden issued Executive Order (EO) 14028, Improving the Nation’s Cybersecurity, which ordered the government to meet or exceed standards and requirements for cybersecurity in these critical areas:
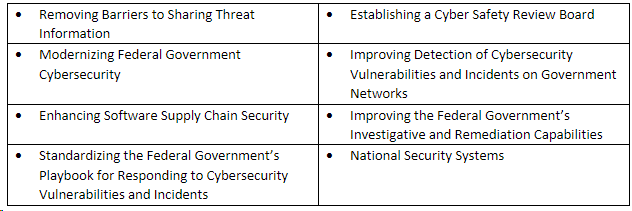
One of the key components in this directive is to implement a Federal zero trust architecture (ZTA) strategy to improve US agency cybersecurity. Detailed information about what’s required for Federal ZTA implementation including the Federal ZTA strategy, the ZTA Maturity Model and the Cloud Security Technical Reference Architecture for ZTA can be found at the Moving the U.S. Government Toward Zero Trust Cybersecurity Principles Web site.
Reinforcing Executive Order 14028, the Office of Management and Budget (OMB) released a strategy and transition Memorandum in January 2022 titled: Moving the U.S. Government Toward Zero Trust Cybersecurity Principles. This memorandum laid out the specific cybersecurity standards and objectives that the agencies are required to meet by end of fiscal year 2024 “…in order to reinforce the Government’s defenses against increasingly sophisticated and persistent threat campaigns.”
The five pillars of the ZTA strategy
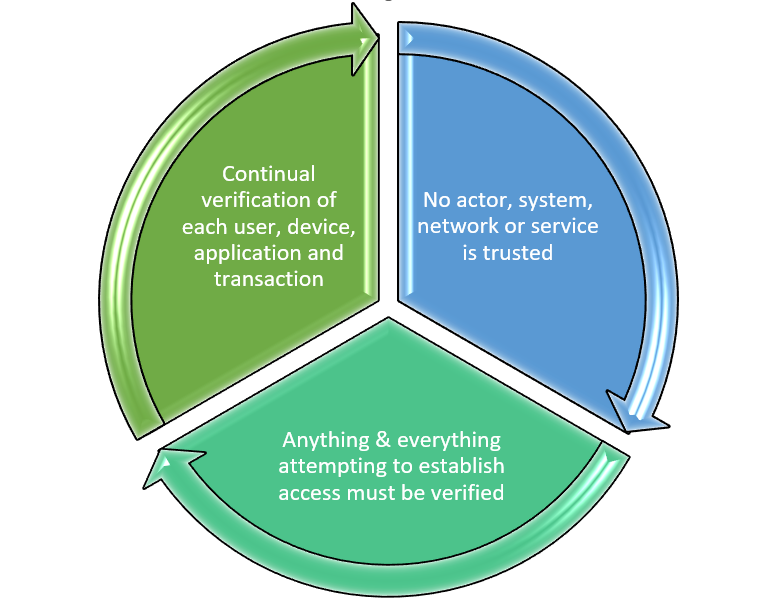
The Federal ZTA strategy envisions a transition to a “zero trust” approach to security that provides a defensible architecture that will as EO 14028 puts it, […defend the vital institutions that underpin the American way of life…]. As referenced in the OMB memorandum, the foundational tenets of the ZTA are:
- No actor, system, network or service operating outside or within the security perimeter is trusted
- Anything and everything attempting to establish access must be verified
- A shift in philosophy of how we [agencies] secure our infrastructure…from verify once at the perimeter to continual verification of each user, device, application, and transaction
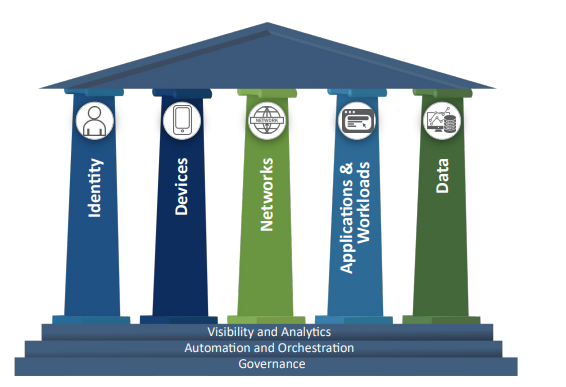
Based on the Zero Trust Maturity Model developed by the Cybersecurity & Infrastructure Security Agency (CISA), the Federal ZTA strategy is based on visions, goals and actions (requirements) that are focused in these complementary areas of effort (pillars)1 as shown in figure 2:
1. Identity: Agency staff use enterprise-managed identities to access the applications they use in their work. Phishing-resistant MFA protects those personnel from sophisticated online attacks.
2. Devices: The Federal Government has a complete inventory of every device it operates and authorizes for Government use, and can prevent, detect, and respond to incidents on those devices.
3. Networks: Agencies encrypt all DNS requests and HTTP traffic within their environment, and begin executing a plan to break down their perimeters into isolated environments.
4. Applications and Workloads: Agencies treat all applications as internet-connected, routinely subject their applications to rigorous empirical testing, and welcome external vulnerability reports.
5. Data: Agencies are on a clear, shared path to deploy protections that make use of thorough data categorization. Agencies are taking advantage of cloud security services to monitor access to their sensitive data, and have implemented enterprise-wide logging and information sharing.
There are three additional themes that cut across and will be implemented in each pillar: Visibility & Analytics, Automation & Orchestration and Governance.
Taken together, these five pillars and three themes are the foundation of how Federal agencies will implement and improve cybersecurity going forward.
Who’s Affected by Federal ZTA Requirements?
ZTA applies to government agencies and all Federal Civilian Executive Branch (FCEB) agencies are required to comply. However, outside entities who deal with the government may also be required to comply with certain aspects of ZTA, including contractors, partners, and their devices, applications and networks that interact with Federal subjects and resources.
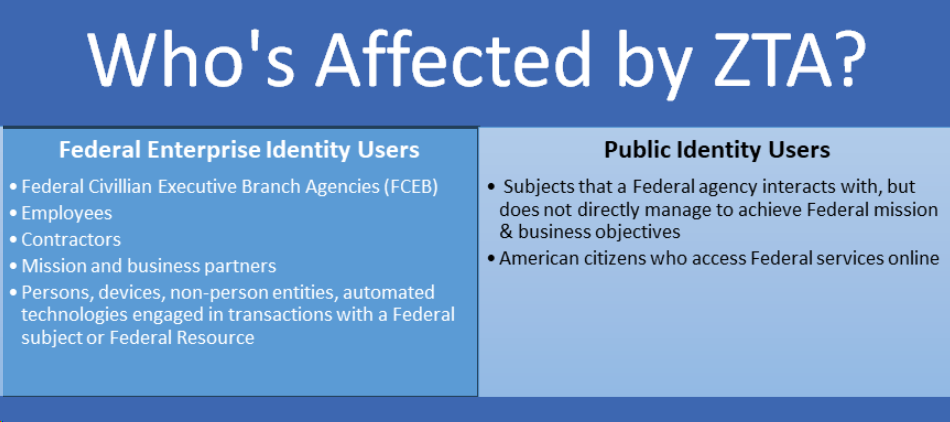
In the January 2022 OMB Memorandum, the term users includes employees, contractors, and enterprise users such as a mission or business partner as defined in another OMB document titled: Enabling Mission Delivery through Improved Identity, Credential, and Access Management. In that document, the term Federal enterprise identity refers to […the unique representation of a subject, for example, a person, a device, a non-person entity (NPE), or an automated technology, that is engaged in a transaction involving at least one Federal subject or a Federal resource, for example, Federal information, a Federal information system, or a Federal facility or secured area.]
OMB also defines a public identity that refers to […the unique representation of a subject that a Federal agency interacts with, but does not directly manage, in order to achieve its mission and business objectives. Public identity may also refer to a mechanism of trust used to render services to the American public.] Public identity users and organizations may find that ZTA requirements will affect how they configure, manage or use equipment or personnel to interact with the Federal government. Conversely, everyday American citizens who access Federal services online may find their access methods increasingly influenced by ZTA requirements.
How ZTA may affect IBM i security & processing
The Federal ZTA strategy is an ambitious strategy with an ambitious timeline. Federal agencies are required to meet specific cybersecurity standards and objectives by the end of Fiscal Year (FY) 2024.
For organizations that operate IBM i servers that directly service governmental agencies, you may find your IBM i servers, services, interfaces, communications and access will be affected by Federal ZTA required actions. Some of the requirements that may affect IBM i servers interfacing with Federal systems or users include:
Authentication and user verification changes: The Identity pillar specifies requirements for using enterprise identity management (EIM) to access applications running on IBM i systems, employing phishing-resistant methods for multi-factor authentication (MFA) and enforcing MFA validation at the application layer, rather than at the network layer.
IBM i administrator user password policies may also have to change as ZTA requires the elimination of special characters in passwords and the elimination of password rotation policies. These requirements conflict against many regulatory, industry and even governmental password composition requirements to contain any three out of four-character passwords (IBM i *REQANY3 password rules) and using the Password Re-use Cycle system value (QPWDRQDDIF) to specify that users cannot reuse recently used password values. This change will require organizations to navigate between ZTA password requirements and other regulatory password requirements.
To meet these needs, IBM i administrators with servers covered under ZTA may have to implement EIM authorization capabilities, possibly using IBM i Single Sign-On (SSO) or another EIM system that can authorize access to IBM i resources. They may also have to evaluate or install an IBM i compatible multi-factor authentication (MFA) solution that offers phishing-resistant MFA authentication methods (more on phishing-resistant MFA in a future blog post).
IBM i-based organizations may also need to evaluate using IBM i exit points or exit point management software such as iSecurity Firewall to handle conflicting password composition requirements between Federal agencies using ZTA and other regulatory entities. Exit point management may be necessary to secure Federal ZTA users that have one set of password policy requirements with industry, regulator, non-Federal government and insurance company entities that have a different set of password policy requirements.
Encryption changes: ZTA contains a number of Network and Data pillar requirements to encrypt network traffic and data. The Networks pillar requires that agencies encrypt all DNS requests, HTTP traffic and email traffic. Agencies must also resolve DNS queries using encrypted DNS, where it is technically supported. Further, organizations must encrypt data at rest for data that resides in the cloud. EO 14028 also specifies that all data must be encrypted while in transit.
To satisfy these needs, IBM i organizations may need to evaluate and implement IBM i-based encryption software. If providing DNS services, using the IBM i for Web serving or providing i-based Web services, DNS, HTTP and Web UI services may need to be modified for encrypted processing.
IBM i-stored cloud data at rest may need to be encrypted using IBM capabilities or a third-party package such as absCompression or iSecurity Encryption. IBM i data in transit capabilities such as backup or vaulting capabilities, FTP routines, downloads to user machines, high availability replication and others may need to be reconfigured to encrypt the data in transit.
These are just a few of the requirements that IBM i organizations may need to meet to comply with Federal ZTA requirements. SEA will publish more information on IBM i-Federal ZTA compliance at a later date.
To Learn More
This blog is an introduction to the Federal ZTA strategy and how it may affect IBM i access and installations. SEA encourages any IBM i shops who may fall under the Federal ZTA strategy initiative to contact the US Federal government for more information about their obligations and IBM i-related Federal ZTA changes to be implemented in 2024.
Please feel free to contact SEA if you have any questions about configuring IBM i security for Federal ZTA compliance or would like to discuss any other IBM i security issue.




