
Threats to Your System: Identifying IBM i Exit Point Vulnerabilities
Exit points provide many benefits to IBM i shops, making it easier to integrate data and applications. However, exit points can also expose your system to potential threats, which if not properly understood, can potentially result in loss of data or a security breach. Having visibility to exit point usage can help improve your system security.
Part of the problem is that it is not easy to know which exit points are being used and by whom. This lack of visibility makes it difficult to know whether your system is really secure or not. SEA’s iSecurity Firewall provides you with an easy way to determine which exit points are being used, who is using them, and what actions they are preforming.
Making Exit Point Usage Visible – The What, Who & When
Understanding which exit points are being used is not easy to do, without a solution like SEA’s iSecurity Firewall. Having visibility to this information is the first step in securing your exit points. The iSecurity Firewall graphic shown below makes it easy for administrators to know which exit points are being used most often, and by which users. You can see in this example that the RMTSRV exit point is used more frequently than any other exit point, followed by Other usage and TELNET access. Once you are aware of which exit points are used most frequently, you can better ensure that they are being used by the right people and that those people are preforming allowed functions.
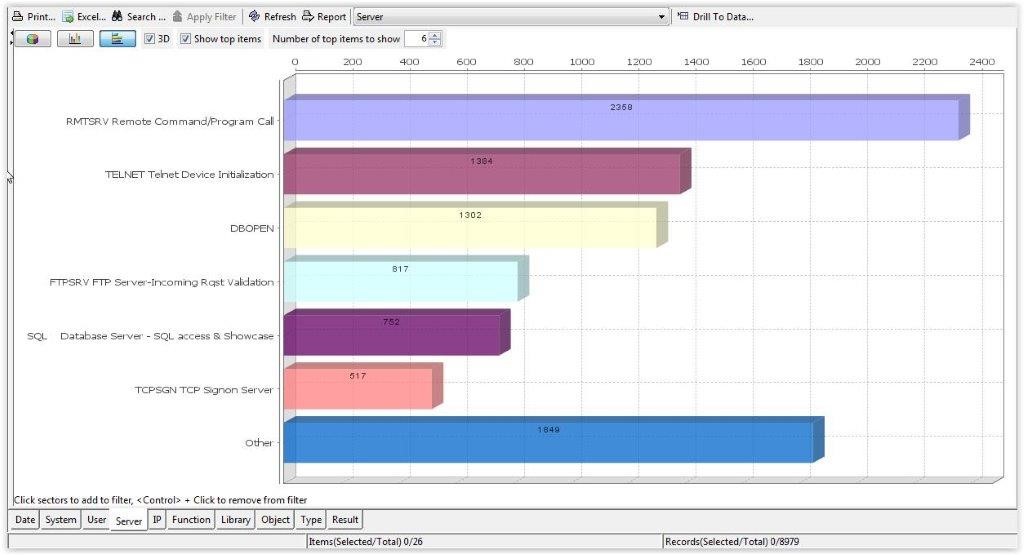
But knowing which exit points are being used most frequently is only the first step. You also need to understand how they are being used to properly secure your IBM i from security threats. iSecurity Firewall provides another view of the information that allows us to see which specific commands are being used most often. This information is a little more informative, because we can see which actions are being performed the most. We see that the RMTSRV command is used most frequently and there are some commands that are used infrequently. This helps identify areas where you may need to lock down specific exit points or which commands can be executed by the user.
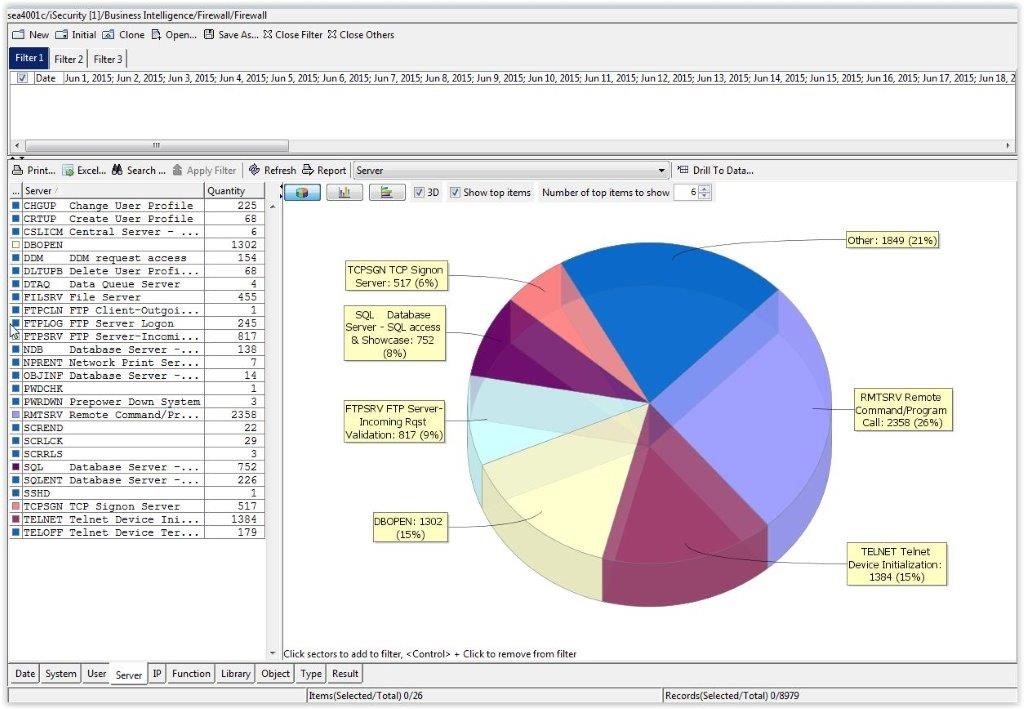
We now know which exit points are being used and which commands are being executed. The final piece of the puzzle is being able to see who is executing commands, and when they are doing it. Using iSecurity Firewall, an administrator can drill down into a specific command and see who used it and when they used it. With this level of detail, you can better understand the risks and threats you face. For example, if there’s a user who is using FTP to access sensitive data in the evening from home, that may put you at risk of data loss. Auditors may also want to see this kind of information, and it’s nice to have it in an easy to understand format. These graphs can also be helpful when trying to troubleshoot a user problem.
Having the Data is the First Step
While understanding the vulnerabilities your IBM i is exposed to through your use of exit points is crucial, it’s only the first step in securing your IBM i. The next step is to use the information the solution provides to prevent the use of exit points that put you at risk. iSecurity Firewall is a single solution that helps you to understand the risks exit points are causing and provides the ability to prevent those actions from occurring in the first place. This is where the true benefit comes into play; being able to prevent potentially harmful actions from happening.




