
IBM i does a great job storing security event information in its security audit journal, QAUDJRN. QAUDJRN is a special IBM i journal that records security related events on your system. Using IBM commands, you can dig through QAUDJRN journal receivers and find information about how your IBM i security is behaving, what objects specific users are accessing, and how users and unauthorized personnel are getting into the system.
But QAUDJRN can’t do everything. It can’t and doesn’t collect information about every possible security event. QAUDJRN can be difficult to work with for the average shop, particularly in the areas of storage, uncollected information, and ease of use. IMHO, these are the three biggest problems with using QAUDJRN for security auditing.
- QAUDJRN journal receivers take up too much disk space
- QAUDJRN journal entries are difficult to analyze and don’t have easy to use analysis tools
- QAUDJRN doesn’t collect everything you need to secure your system
Let’s look at how each issue affects security auditing and what can be done to make auditing easier and more flexible.
Issue #1: QAUDJRN journal receivers take up too much disk space
Every designated security event is recorded in a journal entry stored inside a journal receiver attached to the QAUDJRN journal. When an attached journal receiver becomes too large, it becomes more difficult to analyze what’s happening with security on your system. Large active receivers also affect IBM i performance and take up a lot of disk storage. Because of this, QAUDJRN journal receivers must be periodically detached (removed) from QAUDJRN and replaced with new journal receivers.
To reduce storage, IBM i administrators must set up a regular schedule to detach, save, and delete old QAUDJRN journal receivers. But note that IBM i’s automatic cleanup function that comes with Operational Assistant does not automatically clean up old QAUDJRN receivers. Changing and deleting old journal receivers can be automated within the QAUDJRN itself or it can be performed manually or through a custom program.
If you don’t delete old QAUDJRN receivers on a periodic basis, you start filling up storage. On a system with 30% disk utilization, this may not be much of an issue as long as you remove old journal receivers sometime. But if IBM i disk utilization is running at 80% or more, you could easily fill up your disk and crash the system if you’re not paying attention to QAUDJRN journal receiver management and removal.
Issue #2: QAUDJRN journal entries are difficult to analyze and don’t have easy to use analysis tools
The big problem here is that IBM doesn’t offer enough tools to perform deep system analysis on security events. Your security research and analysis options boil down to:
- Use the Display Journal command (DSPJRN) to look up relevant journal entries
- Use the Copy Audit Journal Entries command (CPYAUDJRNE) to copy selected journal entries into an IBM i file and then use your own custom-written query or program to analyze the entries
- Use SQL to extract audit journal entry data using the DISPLAY_JOURNAL function and analyze the results
It’s difficult to extract and analyze QAUDJRN data, and its journal entries are not accessible to non-technical personnel without custom programming. There isn’t a large set of user reports to run over the data, and there’s no graphical interface for working with the data. And some older commands such as the Display Audit Journal Entries command (DSPAUDJRNE) are no longer being enhanced.
QAUDJRN also can’t alert your staff when a problem is detected. Again, custom programming must be created to automatically alert your staff when an unusual security event occurs.
Issue #3: QAUDJRN doesn’t collect everything you need to secure your system
According to IBM, QAUDJRN is intended solely for security auditing. You can configure QAUDJRN to record journal information about access attempts in the following three security levels.
- System-wide auditing for all user activities
- Auditing activity occurring over specific objects
- Auditing activity that occurs for specific users
With QAUDJRN, you can record two things: 1) what specific users are doing on the system and where they are doing it from; and 2) who is accessing specific objects. QAUDJRN mostly concerns itself with collecting dynamic information regarding user activity as they access system objects.
There’s a problem with what QAUDJRN doesn’t collect: static security changes that auditors and administrators still need to know about. As opposed to the dynamic information QAUDJRN records, static security information includes one-time events or changes over time that can have a big effect on security auditing. Some examples include:
- Files and Libraries that suddenly change or decrease in size, which can indicate unusual activity on the system or in an application
- Historical analysis looking for security access patterns in the last few weeks (trends)
- Changes in object authorities for objects that aren’t being monitored in QAUDJRN, when QAUDJRN is only set up to monitor for specific object access (level 2 monitoring shown above)
- Application security breaches, where unauthorized sensitive fields such as pricing, salaries, and sales discounts are changed without management’s knowledge
All of these items fly under the radar with QAUDJRN monitoring, because QAUDJRN doesn’t record or report on these items. All of which leaves some unfilled security holes in your system.
Beyond QAUDJRN
QAUDJRN is excellent at collecting security information about your system. Its weaknesses occur because of its storage requirements, its lack of an easy to use analysis interface, and its inability to collect static but valuable information.
In my humble opinion, IBM i shops can build on what QAUDJRN has to offer by evaluating and implementing the following types of third-party products. These products are offered by several different IBM i software vendors, not just SEA (we don’t offer the only solution, just the best). They can be used either as a replacement or an enhancement to QAUDJRN, and they provide many of the capabilities that QAUDJRN is missing
- Audit and Compliance Reporting software, such as SEA’s iSecurity Audit product, that helps cut down on journal receiver disk usage, provides real-time reporting and alerting capabilities, provides a collection of ready-made audit reports, collects and reports on static data, and provides a graphical interface for analyzing security data.
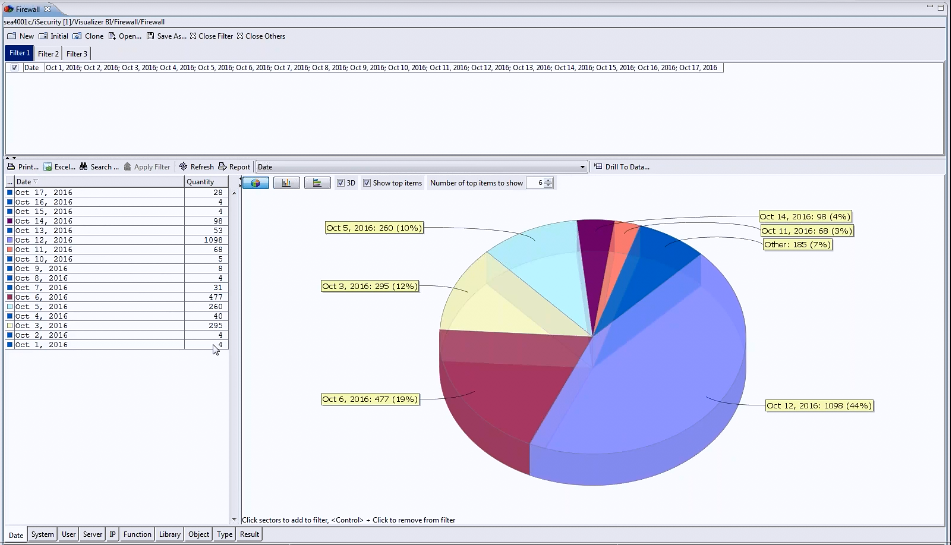
Figure 1: Commercial products like iSecurity Audit provide the graphical interfaces for analyzing security event data that QAUDJRN lacks
- Message and resource monitoring software, such as SEA’s absMessage product, that monitors for resource issues on the system and also provides real-time monitoring for static events.
- Application Security and Business Analysis software, such as SEA’s AP-Journal product, that tracks and reports on database changes and monitors for unauthorized changes that occur when valid users change sensitive file information such as price, salaries, or sales discounts.
Please feel free to contact us at SEA software if you want to learn more about how these products can help your shop fill its own security auditing requirements.




